If you work in cybersecurity right now, you are tired. A typical security team receives about 960 daily alerts, which is, in technical terms, absurd. If you spend 40 minutes investigating each one, that's 640 hours of work every single day. To keep up, you'd need 80 full-time analysts. That's more people than work at my local Trader Joe's, and they can barely keep the Everything But The Bagel seasoning in stock.
Incident response automation exists because the human body cannot be scaled indefinitely. It connects your detection, investigation, and response tools into orchestrated workflows that can triage and enrich alerts, assign priority, and trigger approved actions without waiting for a human to catch up.
Ahead, we'll break down what incident response automation is, how it works, the benefits you can expect, and practical examples you can steal.
Table of contents:
What is incident response automation?
Incident response automation refers to the practice of using software-driven logic (rule-based engines, scripts, and artificial intelligence) to automatically detect, triage, contain, and respond to security incidents with minimal human intervention. It leverages predefined workflows and playbooks, often enhanced by machine learning, to help security operations center (SOC) teams handle threats and IT disasters faster, more consistently, and with fewer mistakes than a human could manage alone.
Automated incident response is typically implemented through SOAR: security orchestration, automation, and response (which sounds like a prog rock band from 1974). A SOAR platform is basically the brain and the hands of your security operation. It connects to all your other security tools (like SIEMs, EDR, firewalls, cloud services, and ticketing systems), and it orchestrates them to work together in a coordinated response when something bad happens.
Let's say a critical security alert hits your dashboard regarding a suspicious IP address attempting to compromise a user account. Without automation, your incident response process probably looks like this:
When the alert comes in, someone (most likely you, sorry) has to manually check half a dozen different systems to figure out if it's real.
Then you have to manually block the bad IP address, manually reset the user's password, manually send an email to your boss, manually update a ticket, and manually cry in your car.
With automation, that whole process can happen in seconds:
The system detects the threat and enriches the alert with context (like recognizing an IP address that is known for hosting malware).
It takes action by blocking the IP, isolating the compromised endpoint, resetting credentials, and notifying everyone who needs to know, all before you even finish reading the first alert.
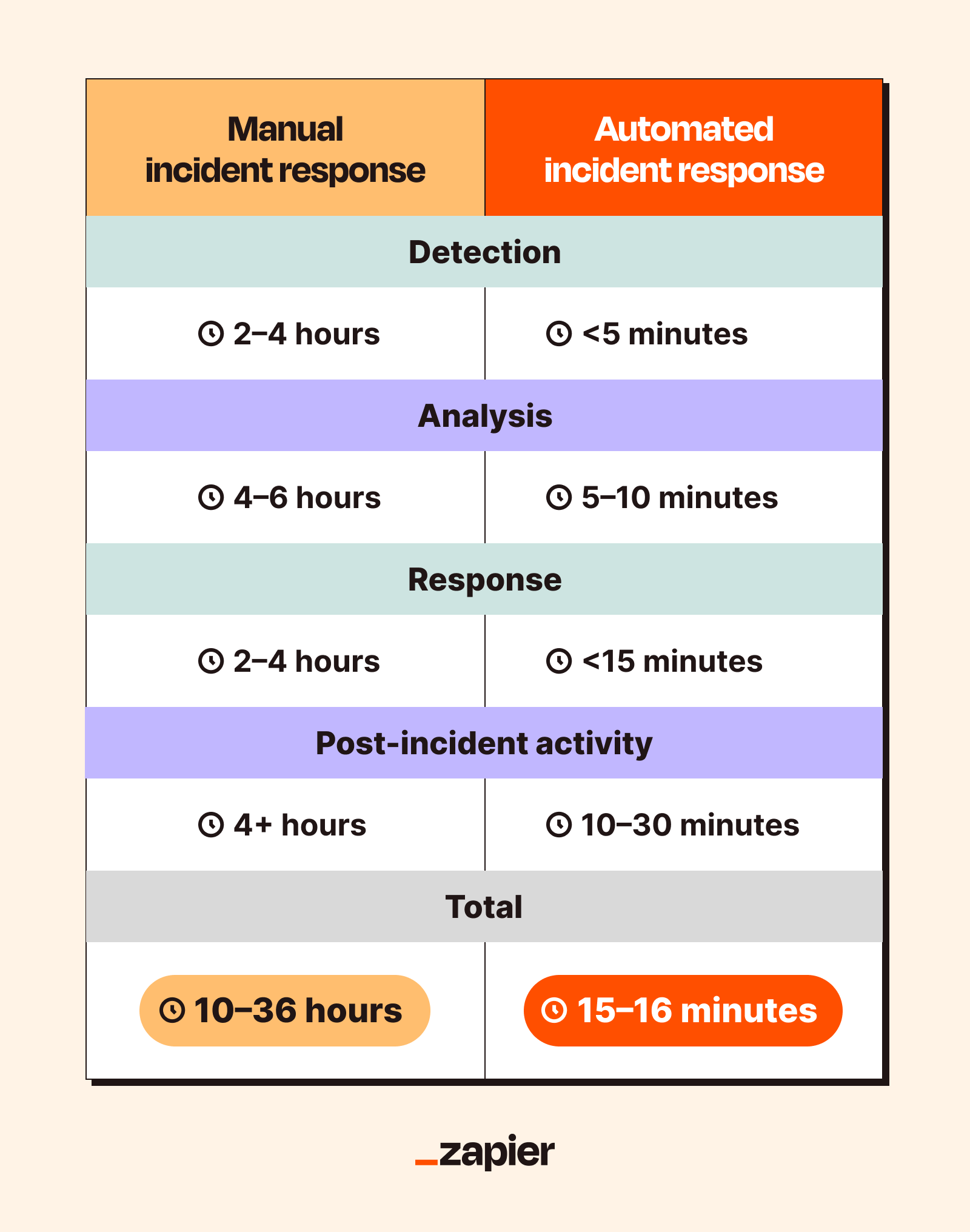
The point of all this is to reduce mean time to resolve (MTTR), which is how long it takes from "Oh no, something's wrong" to "Ok, we fixed it." Traditional manual incident response is super slow because humans are super slow. (I say this with love, because I am also super slow.) Modern attacks are fast. Threat actors can move laterally (jumping from one compromised system to another) in minutes. If you're waiting for a human to manually investigate and respond, you're basically bringing a pool noodle to a swordfight.
How does automated incident response work?
Incident response automation follows a set process. Each step builds on the one before it, forming a pipeline between detection and resolution while eliminating unnecessary delays. Let's break down how it works.
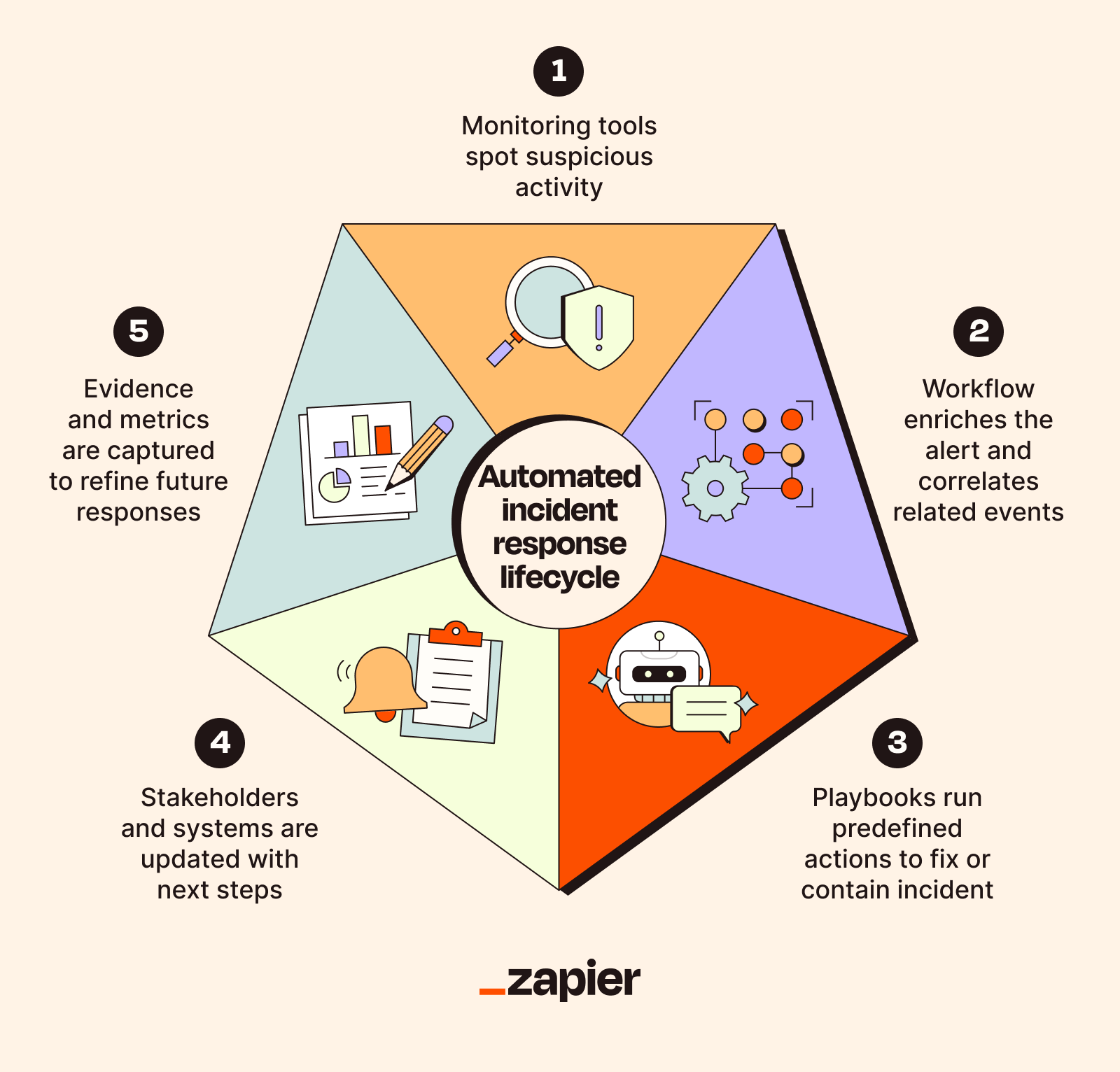
1. Detection
Everything starts with detection. Your monitoring tools are constantly on the lookout for trouble. When something suspicious happens (like an attempted login from Estonia by a user who's supposed to be in Ohio, or a file that suddenly starts encrypting everything on a hard drive after years of quiet obscurity), the system generates an alert.
When something triggers an alert, that signal gets sent to your automation platform. This is the spark that lights the fire. The system doesn't wait for a human to notice the alert. It picks it up instantly and starts the next phase.
The key here is integration. Your SOAR automation platform needs connections to all your detection tools. Without those connections, alerts fall into silos. With them, every warning feeds into a single automated pipeline.
2. Analysis and classification
Once the alert is triggered, the automation platform doesn't just panic and start shutting everything down. (That's just what I'd do.) Instead, it enriches the alert with context to figure out if it's a real threat or a false positive. It might query reputation databases, check threat intel feeds, or look up the related user in your directory.
Then it assigns a priority based on predefined rules. For example, if the IP has been flagged by at least three threat intel sources and it's trying to access your financial database and it's coming from a country you don't do business with, it's probably critical. But if the IP belongs to your known security scanner and it's just doing its weekly scan, everything's most likely fine.
3. Automated response
Once the system has analyzed the alert and decided it's a real threat, it takes action based on established playbooks. These playbooks provide automated, step-by-step instructions for handling specific incident types without requiring human approval. (Actually, for some actions, you'll want human approval. We'll get to that.)
The type of action depends on the type of incident and how confident the system is that it's making the right call. Common automated responses include:
Isolating endpoints: If a device is infected with malware, the system can immediately disconnect it from the network to stop the malware from spreading. The computer can still talk to the security tool for investigation, but it can't talk to anything else.
Blocking IPs or domains: If a malicious IP address or website is detected, the system can automatically push blocking rules to your firewall or proxy so no one else can access it.
Quarantining emails: If a phishing email is detected, the system can automatically quarantine and delete it from everyone's inbox before anyone clicks on it.
Resetting credentials: If a user's password has been compromised, the system can force a password reset and kill all their active sessions so the attacker can't keep using the account.
Running diagnostics: For IT operations, automation can handle service crashes by restarting the service, collecting logs, or even rolling back a faulty code deployment.
4. Notification and escalation
Just because the system is handling the response doesn't mean humans are completely out of the loop. Incident response automation tools can notify the relevant people—usually via Slack, email, SMS, a ticket in your IT service management system, or all of the above.
The notifications are smart, too. The system knows who's on call, who has the expertise to handle this type of incident, and who just needs to be kept in the loop. So your CISO gets a high-level summary, the SOC analyst gets all the technical details, and that guy in Finance who keeps clicking on phishing links gets absolutely nothing because he doesn't need to know.
Escalation follows predefined rules. For example, a critical incident on a production server goes straight to the on-call engineer with an urgent page, while a low-priority warning might just create a ticket for the morning shift to review.
The system also logs everything—every action taken, every decision made, and every piece of data collected. This creates an audit trail that's super useful for post-incident reviews, compliance requirements, and also for when your boss asks, "What the heck happened last Tuesday?" and you can pull up a full report instead of just shrugging and saying, "IDK, computers are hard."
5. Post-incident activity
The incident is resolved (or contained, or investigated, or otherwise persuaded to stop ruining everyone's day), but the work isn't done. Post-incident activities ensure you learn from each event and improve your defenses for next time.
Evidence collection happens throughout the response, but the post-incident phase is when you organize it. Logs, screenshots, memory dumps, and network captures all get packaged together. This evidence supports forensic analysis and legal requirements.
Automated reports summarize what happened, what worked, and what didn't. These reports feed into metrics like MTTR, helping you track improvement over time.
The incident response tool feeds data back into itself to create a learning loop. Closed cases are dissected for pattern and recurrence. If certain alerts are almost always false positives, it can update the rules to filter them out. Or if a particular attack technique keeps appearing, it can create a new playbook to address it on purpose rather than by accident.
All of this amounts to a feedback cycle that makes your automation smarter over time. Each incident teaches the system something new, playbooks evolve, detection rules narrow from broad suspicion to calibrated judgment, and your security posture gets stronger with every response.
Incident response automation benefits
Let's dispel the myth that incident response automation is merely a time-saver. Here's a selection of other advantages you can expect:
Improved detection: Automated incident management constantly monitors for threats, 24/7, even when you're asleep, on vacation, or pretending to work from home. It can correlate data from multiple sources faster and more accurately than a human, which means it catches threats before they grow legs and walk off with your data.
Faster response: Automated threat intelligence reduces your MTTR from hours or days to minutes or even seconds. When ransomware is detected, every second counts. The faster you can isolate an infected system, the less damage it can do, and automation gives you that speed.
Reduced analyst workload and alert fatigue: Remember those 960 daily alerts I mentioned? A huge percentage of those are false alarms or routine stuff that doesn't actually need human attention. Threat intelligence automation absorbs the low-grade stuff so analysts don't have to. Imagine the joy of being bored because everything is working as intended.
Proactive defense: With machine learning and AI integration, automated systems can predict threats before they fully develop. They can spot early warning signs, like unusual login patterns or suspicious network traffic, and take action before the attacker can do any real damage.
Fewer errors and more consistency: Humans make mistakes. We skip steps when we're tired. We forget to update the ticket. We accidentally block the CEO's IP address because we weren't paying attention. Automation follows the same process every single time, without variation, which means fewer screw-ups and more reliable incident handling.
Stronger, continuously improving security posture: The whole incident response process is an ongoing improvement project that compounds over months and years. If that sounds dull, good. Security should be dull. The thrilling bits are what you're trying to prevent.
Practical incident response automation use cases
Incident response automation covers a variety of use cases that deliver real value. Below are some real-world examples because I respect you too much to waste your time.
Phishing detection and response
Phishing remains the number one attack vector, because people are trusting and tired and sometimes that email that says "URGENT: Your Amazon account has been compromised, click here immediately" looks really convincing.
Luckily, phishing is also a perfect candidate for automation because the response steps are well-defined and repetitive:
When your email security gateway flags a suspicious message (or when a user reports one), the system automatically extracts key data from the email, like the sender's address, any URLs or attachments, and authentication results (SPF, DKIM, DMARC).
Those extracted URLs get checked against threat intelligence databases. Attachments get analyzed in a sandbox environment. The system then calculates a risk score based on what it finds.
If it's confirmed to be malicious, the system automatically searches every mailbox in your organization for that email and deletes it before anyone else can click on it. It also blocks the sender's email address, and URLs get added to your proxy's blocklist. If any user clicked a link or opened an attachment, the system flags that device for deeper inspection and potentially triggers a password reset.
If credentials might have been compromised (like if the phishing page was a fake Microsoft 365 login), the automation can immediately reset the affected user's password and kill all their active sessions.
Finally, it sends a notification to the security team and, if applicable, the user who reported the email, and logs everything for compliance.
All of this happens in a fraction of the time it would take a human to manually hunt down and remove the email from everyone's inbox. This is also where a tool like Zapier can fit in beautifully.
You can use Zapier to connect your email security tools, ticketing software, communication apps, and threat intelligence feeds to build these automated security workflows, even if you don't have a full SOAR platform. Zapier's IT automation capabilities mean you can set up triggers and actions across hundreds of apps, so when a phishing email is detected in one system, Zapier can automatically create a ticket, post to your security channel, and even update your internal documentation.
Streamline incident response communication by kicking off the process and alerting your team.
Alert triage and false-positive reduction
Not every alert is a real threat. In fact, most alerts aren't real threats. They're usually a bunch of nothingburgers generated by overly sensitive detection rules, benign activity that looks suspicious, or tools that are just...kind of not good at their jobs.
Automation helps by:
Correlating alerts from multiple sources to see if they're related
De-duplicating identical alerts so you don't get 50 notifications about the same thing
Enriching alerts with context (like "this IP is our known vulnerability scanner, not an attacker")
Auto-closing alerts that are clearly benign based on predefined rules
This means analysts see fewer alerts overall, but the alerts they do see are higher quality and more likely to be real threats.
Malware and ransomware containment
Ransomware is an absolute nightmare scenario. It spreads fast, encrypts everything, and demands a ransom to decrypt your files. (And even if you pay, you might not get your data back, because criminals are, shockingly, not trustworthy.)
Automated malware containment often works like this:
Your endpoint detection tool (EDR) detects suspicious behavior. Maybe a process is trying to encrypt a bunch of files, or it's communicating with a known command-and-control server.
The incident response automation immediately evaluates the alert. If confidence is high (this really looks like malware), containment starts without waiting for human approval.
The affected host gets isolated from the network. The EDR agent severs network connections while maintaining a management channel, meaning the malware can't spread to other machines, but your team can still investigate.
The automation blocks the malicious IP addresses or domains at the firewall level to prevent other systems from getting infected.
It captures forensic data (memory dumps, logs, file hashes, etc.) before it can be overwritten so your team can analyze what happened.
The system kicks off a full scan of the endpoint using antivirus or EDR tools to identify and remove the malware. Additional scans run across your network to check other endpoints for the same indicators of compromise. If the malware has already spread, you'll know quickly.
Finally, it notifies the security team and creates a detailed incident report.
All of this happens in the time it would take you to even realize something is wrong in a manual scenario. And the faster you contain ransomware, the less damage it can do. We're talking about the difference between one infected laptop and your entire file server being encrypted and backups destroyed.
Vulnerability and patch orchestration
The problem with vulnerabilities—security flaws in software that attackers can exploit—is that they never stop coming. Ever. (There's a reason Microsoft made Patch Tuesday a thing.) Keeping up with patching is a massive undertaking, especially in large environments with thousands of systems.
Incident response automation turns vulnerability and patch orchestration from a chaotic, reactive scramble into a structured, proactive process:
Here's how it works:
It begins, as all sensible endeavors do, by collecting the facts. Your vulnerability scanner finds issues, your asset management software knows what's installed where, and threat intelligence feeds track which vulnerabilities are being actively exploited. Automation ties it all together in a beautiful tapestry of impending doom.
Your automated system enriches that data with context. For instance, a critical vulnerability on a test server in an isolated network is lower priority, while a medium-severity bug on an internet-facing production database should probably go to the front of the line.
The automation takes all this context—the CVSS score, asset criticality, exploitability, business impact—and prioritizes it so you know which fires to put out before your entire infrastructure burns to the ground.
Patch deployment can be automated, too, with appropriate safeguards. For standard workstations, patches might roll out automatically after testing. For critical systems (like your payment processing servers, for example), the automation creates a change request, routes it to the appropriate approvals, schedules it for a maintenance window, and then executes it. Some advanced setups can even test patches in a staging environment before rolling them to production.
Integration with ITSM platforms ensures proper change management. Instead of blindly pushing patches to production, they follow approval workflows, generate documentation, and get tracked through completion.
Automated diagnostics and remediation
The thing about IT incidents is that a huge percentage of them are boring. Not "boring" as in unimportant. They're definitely important—your business is literally losing money while that service is down—but "boring" as in predictable. Maybe a service crashed because it ran out of memory, or a server filled up its disk space because log files grew too large, and no one set up log rotation properly.
Automated diagnostics address the most common IT incidents with predefined workflows.
For IT operations, automation can handle common infrastructure and application issues. For example:
When a service crashes, the automation restarts it and checks if it comes back healthy.
When a server runs out of disk space, the automation clears temporary files or expands the volume.
When an application throws an error after a deployment, the automation rolls back to the last stable version.
When a health check fails, the automation runs diagnostics, collects logs, and attaches them to a ticket before a human even looks at it.
This kind of self-healing infrastructure reduces downtime and doesn't require manual work. Your on-call team still gets notified, but by the time they check their phones, the issue might already be resolved.
For problems that can't be fixed automatically, the diagnostics still save time. The ticket comes pre-loaded with health check results and relevant logs, so the engineer knows exactly where to start troubleshooting.
Cloud environments benefit especially from incident response automation since auto-scaling can respond to load spikes by adding capacity, failed containers can be replaced automatically, and health checks can route traffic away from unhealthy instances.
Post-incident reporting
Writing post-incident reports is the worst because you have to reconstruct everything that happened during a crisis when you were probably running on adrenaline and borrowed time. You're supposed to remember exactly what time you ran which command and why you made certain decisions, all while making a frantic, chaotic event sound professional and coherent.
Incident response automation can generate these reports automatically, pulling together:
A timeline of events
All actions taken by the automation and human responders
Affected systems
Evidence collected during the investigation
Resolution details
Metrics like detection time, response time, and resolution time
Recommendations for improving future responses
These reports are invaluable for IT audits and compliance (especially if you're in a regulated industry), postmortems, demonstrating to leadership that your security team is doing its job, and remembering what your family looks like instead of spending the next week writing documentation.
Automate and orchestrate your incident response with Zapier
You don't need a massive budget or a dedicated security team to benefit from incident response automation. Zapier can help you orchestrate security workflows that connect your IT tools, creating automated responses tailored to your environment.
Zapier works as an integration layer between thousands of apps. It can connect your monitoring tools, communication platforms, ticketing systems, and IT management software into orchestrated workflows. When something triggers in one system, Zapier can automatically take action in others.
You don't have to choose between expensive SOAR platforms and doing everything manually. Zapier offers a middle ground: powerful IT automation that connects your existing tools without requiring a team of engineers to maintain.
Related reading: