The cybersecurity threats facing businesses continue apace, and one of the fastest growing threats to both SMBs and enterprise organizations is the business email compromise (BEC) attack.
According to the Verizon 2023 Data Breach Investigations Report (DBIR), BEC attacks "now represent more than 50% of [social engineering] incidents," and "the median amount stolen from [BEC] attacks has also increased over the last couple of years to $50,000." The FBI attributes $3 billion of its estimated total $10.2 billion in cyber attack losses to BEC attacks.
So the threat of BEC attacks is on the upswing, and they're getting costlier. It's worth understanding more.
What is a BEC attack?
We've come a long way from the Nigerian prince emails, but that type of scammy email is the core of what a business email compromise (BEC) attack is. BEC is the more sophisticated version.
Bad actors send emails to business email addresses that spoof a trusted source and make a routine work request. They rely on people working quickly and having a higher trust for emails sent to their business address rather than a personal one. Experienced bad actors might also infuse their request with a sense of urgency or try to elicit fear. They hope that by injecting an emotional component, the recipients lower their defenses and act quickly without scrutinizing the request.
Here's a perfect example of the type of routine business request that bad actors would spoof in a BEC attack.
I recently got an email from a third-party vendor telling me that my client Zapier had switched its invoice and payment system. I needed to click through to enroll, which would require sharing my social security number and bank account information.
Did I click through? I mean, I want to get paid, right?
No, I did not click through.
I emailed my editor at Zapier for confirmation the email was legitimate. As she was on a well-deserved vacation, did I get impatient and move forward before hearing back? Again, no. But once she let me know it was legit, I enrolled.
This email was authentic, but that's how a BEC attack could look.
How BEC attacks work
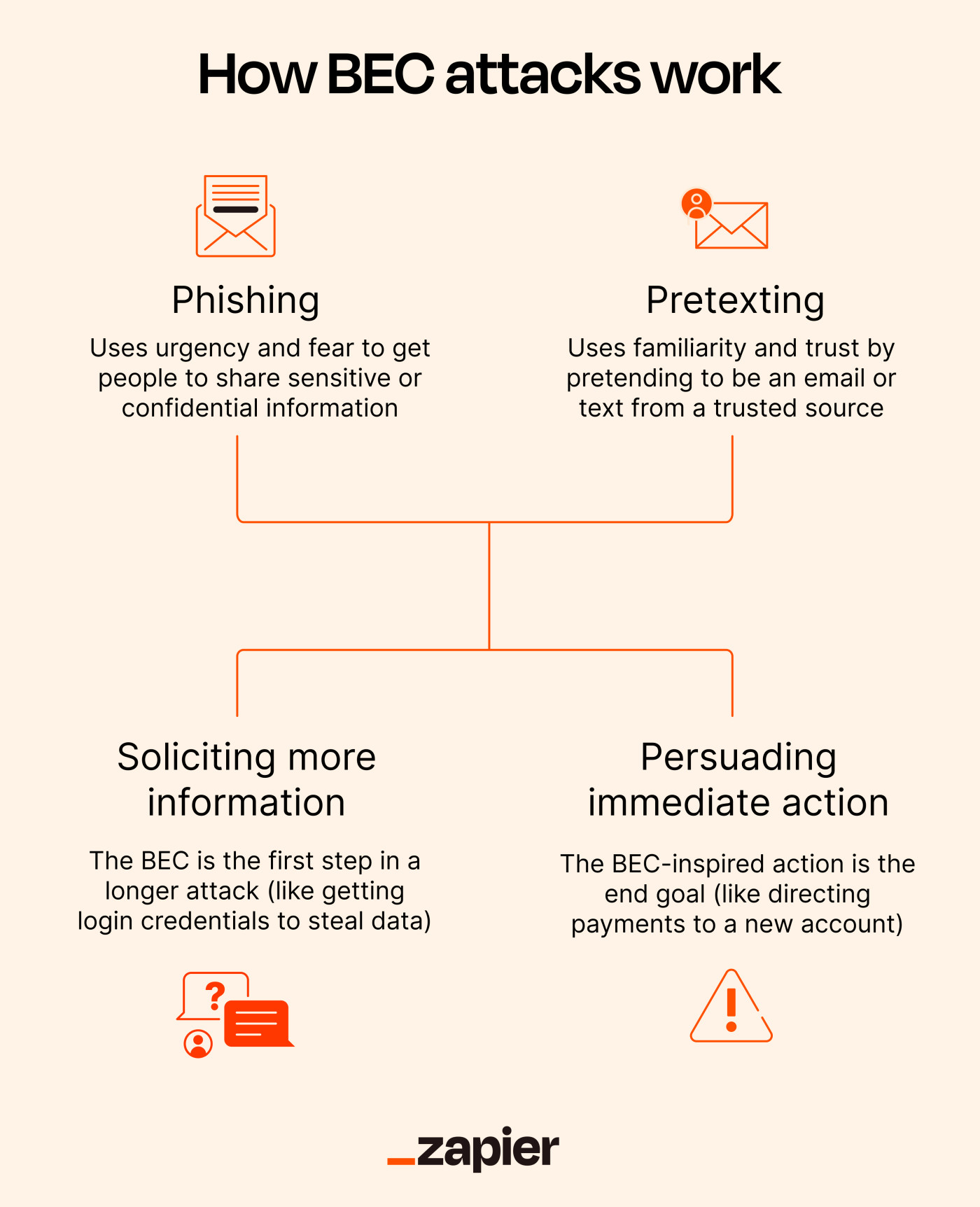
BEC is a form of social engineering because it relies heavily on manipulating humans. BEC emails often use different emotions, such as familiarity, urgency, fear, or wanting to be helpful.
Phishing and pretexting are the main methodologies used in BEC attacks.
Phishing often uses urgency and fear to get people to share sensitive or confidential information. For example, the email might direct you to a spoofed website to capture your login credentials or other valuable information.
Pretexting uses familiarity and trust by pretending to be an email or text from a trusted source, but it might also tap into emotions too. The bad actors design the communication to look like it's from your boss, your company's CEO, a vetted supplier, or any number of roles. Indeed, Verizon's 2023 DBIR report states that the rise in social engineering attacks is "largely due to the use of Pretexting, which is commonly used in BEC, almost doubling since last year."
Common BEC attack paths
The BEC scam path starts with phishing or pretexting. Then it usually proceeds in one of two ways.
Soliciting further information
In this path, hackers request more information they can use to effect further mischief. Here, the BEC is one step in a longer attack.
Stealing login credentials is a common goal of the BEC email. They'll log in to the app that puts them into your company network and go from there. They might install malware, launch a ransomware attack, or steal data. Once they're in, there's a lot of havoc they can wreak.
Another common scenario is getting an employee's email credentials. They can now log in to the company email and mine the address book and conversations to better impersonate and target others at the company.
Persuading immediate action (usually financial)
In this path, the BEC-inspired action is the end goal. For example, a fake email or invoice from a supplier that provides notice of a change in their banking details, which will direct future payments to a hacker-controlled bank account. Sending HR a fake email purportedly from an employee requesting to change their payroll bank account is another frequently used BEC attack.
Common BEC profiles: Who's getting targeted, and who are hackers pretending to be?
There's no end to hacker creativity. While these profiles are common in BEC attacks today, stay vigilant if an email comes from another source but carries other BEC attack characteristics.
Who gets BEC emails?
Anyone with authority to send money or update financial information.
HR and payroll personnel who have access to sensitive information.
Rank-and-file employees who can be an entry point to access those with more authority. These employees may also be easier to motivate by fear.
Who are BEC emails pretending to be?
Suppliers and other external partners who are sending fake invoices and/or updating financial information.
C-suite or senior management sending emails to junior employees. These emails often combine urgency with inaccessibility, e.g., "I'm going to meetings all afternoon, just get this done." And the "this" is sending sensitive information to what looks like a legitimate recipient or website, or facilitating what appears to be a legitimate financial transaction.
Attorneys who need personal or company confidential information.
An employee sending new payroll bank account info to HR or the payroll department. This is called payroll diversion, and it's a growing segment of BEC attacks that's earned its own name.
Defending against BEC attacks
BEC attacks are so insidious because they can be hard to detect. But it's not impossible. Prevention is always better than remediation, but you have defenses in both areas.
Human prevention
Since BEC is a very human attack, employees are a vital layer of defense.
Your cybersecurity training for employees should already include phishing and social engineering awareness. Add information specific to BEC, including helping them detect pretexting. Train them on common BEC scenarios and how a BEC attack might look based on the role they have at the company.
You should also train them on your company's BEC incident response policy, with emphasis on what steps they should take if they receive a concerning email. Of course, this means creating a company BEC response policy first. Steps in a BEC incident response policy could include:
Don't engage with the email in any way.
Try to verify its authenticity by contacting the purported sender outside of that email and through as direct a contact channel as possible. For example, don't call a supplier's general line. Have the direct phone number to the person who manages your company's account.
If authenticity can't be verified, provide notice to designated IT and security personnel.
Don't let it fester. Try to authenticate immediately, and if it can't be verified, contact the people within the company tasked to respond to a possible BEC attack.
An employee may complete a transaction or send information and then become concerned. Make sure employees understand that the best thing for them to do is provide immediate notification.
Also look at your company procedures for managing invoices and payment requests, updating financial information, and sharing personal or confidential information. Ask yourself where you could add some checkpoints or safeguards into the existing workflow that make it less likely the fraudulent request would be fulfilled.
For example, for the policy when HR or payroll gets a request to update an employee's bank information, the standard response might be to confirm the request with a new email to that employee's email address (instead of replying directly to the request) or to contact them through another internal company communication channel.
Technology prevention
Several common cybersecurity defense practices can also offer another layer of defense. Start by strengthening access control to your network:
Review permission levels, and never give a user more access than they need to any system.
Segment your network, so if hackers get an employee's credentials, they won't be able to go everywhere.
Keep all operating systems and software up to date and fully patched.
You can also use end-point security, anti-phishing, and email filtering software to help reduce the chance a BEC email gets to the intended recipient.
Rapid detection and response
Alright, what to do once the fox is already in the henhouse. The good news regarding financial BEC attacks is that you might not lose any money if you can act quickly once the fraudulent financial transaction has begun.
Quick reporting is always important in any cyber incident. The people tasked with managing a BEC attack response should contact your financial institution to try canceling the transaction while it's still pending there.
You can also file a complaint with the Internet Criminal Complaint Center (IC3), which is part of the FBI. The IC3 has a recovery asset team (RAT) that coordinates with law enforcement and financial institutions to prevent a transaction from completing. It calls the process the Financial Fraud Kill Chain (FFKC), which is much better than RAT.
According to the FBI, the FFKC successfully put a monetary hold on 73% of the domestic-to-domestic transaction BEC complaints. The frozen transactions totaled $433 million.
Unfortunately, the other 27% of reported transactions represented $590 million in losses.
In a BEC attack, quick reporting to the FBI may also help recover any lost funds. I'm saying there's a chance.
Stay frosty
Effective cybersecurity is always chasing an ever-moving target. Maintaining the fundamentals of good cybersecurity hygiene will help protect you and your business from a BEC attack.
Still, we always need to understand where the new threats are coming from and update our cyber security defenses accordingly.
Related reading: