You might not believe me, but security teams really do want to help make security as simple as possible for you. Seriously.
At Zapier, our new employees want to get up to speed quickly. On their first day, they want their tech configured just right before they dive in to all their onboarding tasks. And there's nothing more tedious than waiting on human approval while setting things up—especially if the thing you're waiting for is the VPN that gives you access to almost everything else.
That's why our security team tries to make things as self-serve as possible. For a long time, our VPN setup let users log in with their email address to get a VPN profile. The issue, from a security perspective, was that there was no offboarding process to this and the monitoring was limited.
So we took away passwords.
Why use a VPN without passwords?
A big pain point to productivity in general is constantly repeating yourself—this is particularly true when it comes to passwords. Single sign-on (SSO) is helpful in most scenarios because you can set up a workflow to log in to systems by just clicking through. This seems to be a winning scenario: even though the user is prompted somewhat often, the workflow is pretty unobtrusive.
The same logic applies to a VPN. Most VPNs allow a user to save a username and password, but if you enforce multi-factor authentication (MFA), users will generally have to manually enter a code each time they want to connect. Most common scenarios for this involve pulling up a phone or alternate device, waiting for it to load the tokens, then typing the code in the program. We wanted to avoid all of this and make it fairly painless for Zapier employees. We decided YubiKeys and certificates would work best.
Logging in to the VPN is streamlined now. The user essentially goes through a one-time setup to log in with their SSO, after which they sync their YubiKey. This provides them with a profile that they can use, meaning there are no passwords going forward.
Just hit connect, tap your YubiKey when prompted, and you're in.
How do onboarding and offboarding work?
So, what does this look like for Zapier employees? Streamlined, I like to think.
The process is essentially:
Go to the VPN setup webpage.
Click Log in with SSO. (During onboarding, this would have already been set up, so this step basically just passes through.)
Tap your YubiKey to synchronize it to your new profile.
Download a .zip file that contains your unique VPN profile (with unique certificates bundled in).
Load the profile into the VPN software (anything that is OpenVPN compatible).
Sign in with your username (no password) and click Save username, so that it's no longer needed
Tap the Yubikey.
That's all!
From here on out, they can simply click the icon and tap the YubiKey.
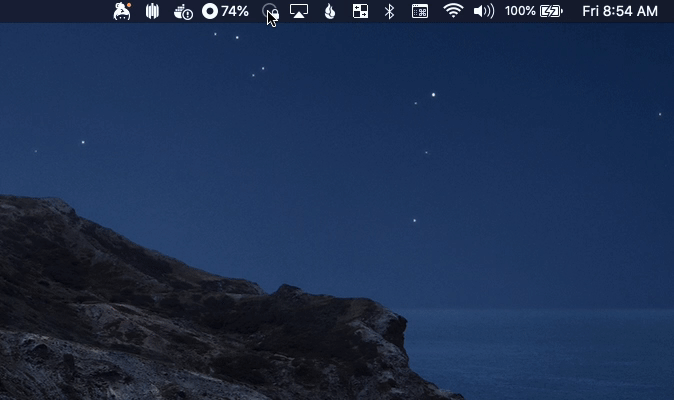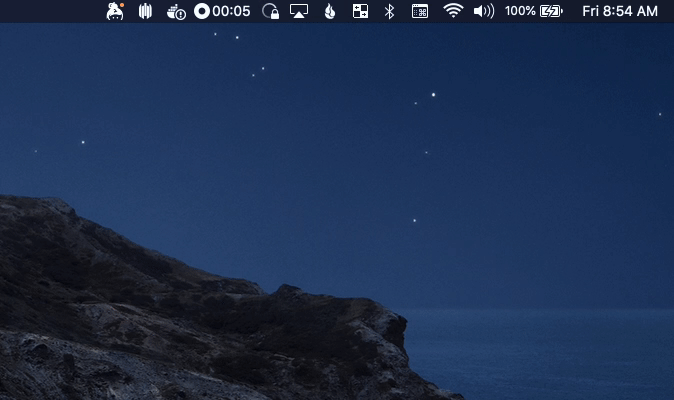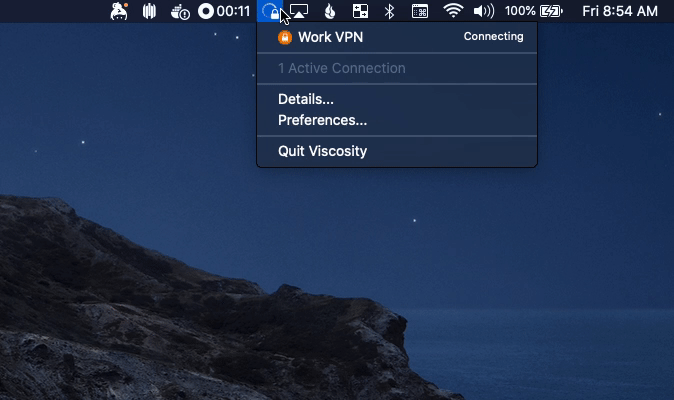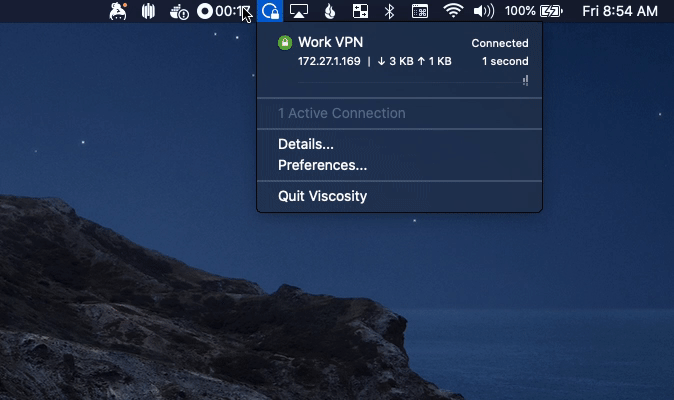
The offboarding experience is also automated now because it's tied to the employee's SSO.
By offboarding the user and disabling their user account, an automated process that runs beside the VPN server gets a signal to disable them as well as create an archive of their audit logs into a safe place in case there are any incidents later. The user is immediately disconnected and disabled by certificate revocation. This means no one who leaves the company has lingering access to our networks, all without any additional overhead.
Can exceptions be made for temporary access?
Absolutely. We have a playbook for users that are affected by logistics or malfunctioning YubiKeys. (Employees are still required to be an active single sign-on user, so there's no risk of external actors asking for credentials directly.)
When an employee asks for an exemption, the security team creates for them a VPN profile with certificates—but also a password. The onboarding process here is the same, except that they will temporarily have a password. While it's not ideal, it does give some protection against the VPN profile being shared by mistake or with malicious intent. The profile has valid certificates, but people using it will also need the password.
From here on out, an automated process will notice that we have users without a YubiKey for multi-factor (this means they're a direct exemption) and remind them weekly to make sure they have a YubiKey on order. After four reminders (one month) it will disconnect and remove them from the VPN by revoking the certificate and letting them know to ask for another exemption. This lets the security team be aware of users that are constantly asking for exemptions.
How is this secure?
This isn't much different than most enterprise-grade VPN solutions, in that we rely on certificates. We feel much more confident knowing that the process is easy enough and unobtrusive to the user.
Security involves trade-offs, and in this scenario, we decided to trade a human process that affects productivity for something that feels more natural. Instead of relying on insecure MFA methods such as SMS or MFA apps—which are hard to control from a security perspective—we chose a hardware-based solution that prevents cloning or intercepting.
Of course, the risk of losing a YubiKey is very real, so we typically recommend one that stays inside the laptop. That means if the employee loses their laptop, they will lose their hardware token, but typically the turnaround time here for responding and revoking is faster than with a phone. For starters, we don't issue phones, and phones generally go missing more often than laptops, meaning that users will delay reporting a missing phone (for MFA) versus their entire workstation.
What does the monitoring and maintenance look like?
Part of the reason that we chose our VPN solution is that it's extremely easy to set up and supports high availability. Adding new servers is automated in our cloud by simply scaling up.
Monitoring is a web application that sits beside the VPN in our cloud and is extremely simple and lightweight. It produces metrics from the database such as:
Number of total users
Number of users connected
Number of hosts
And other related metrics.
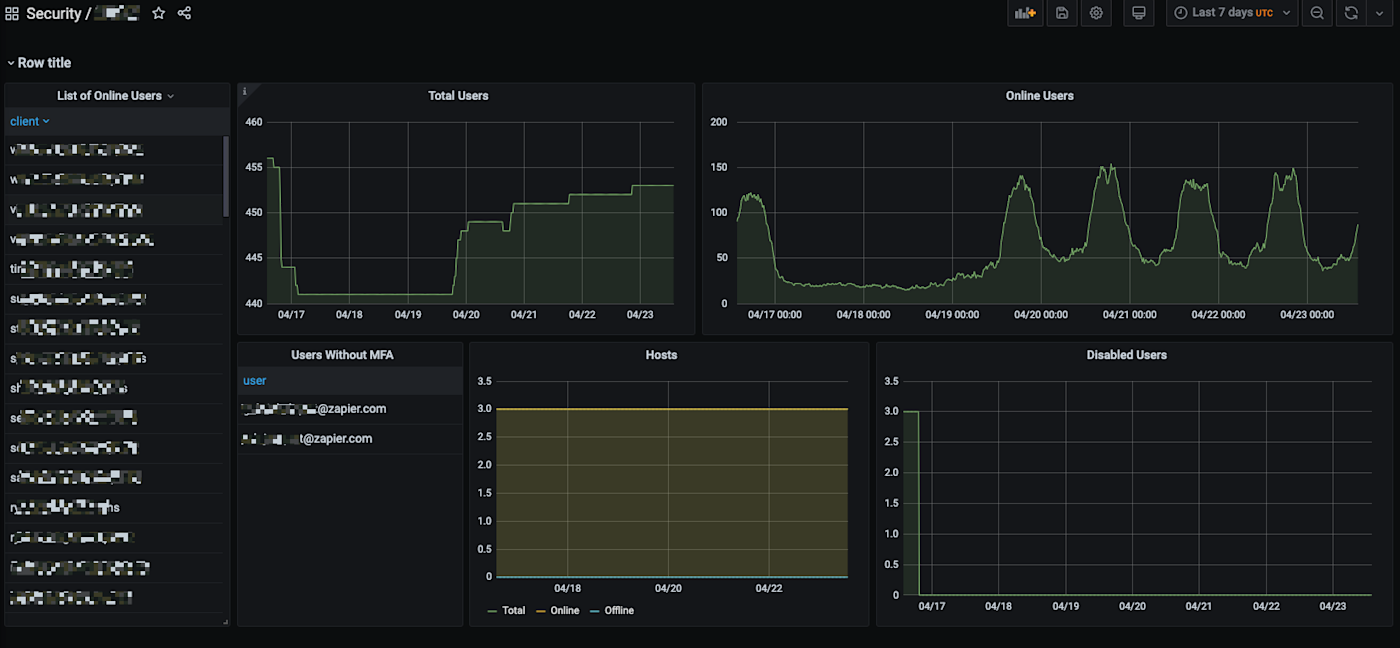
Adding new metrics and visibility is extremely simple, which was our guiding principle for choosing a solution. The VPN itself also has an API that we could leverage for additional automation and workflows.
In addition to custom metrics, we also get infrastructure metrics and alerting out of the box, since this particular application is hosted in Kubernetes. We can see things such as the number of hosts running (the pods are 1:1 with hosts and scale together) and hosts that are throttling, oversaturated, or in general performing poorly. With this, we can scale and monitor the same way we scale and monitor our production applications.
And that's our setup. We're proud of how it balances our employees' needs with our security needs, and we hope it's helpful for you to make decisions for your team as well.
Read more: