I remember when securing a company network meant installing a solid firewall, updating your antivirus once in a blue moon, and calling it a day. Your company data was safe, and you'd sleep soundly at night knowing your network perimeter was holding strong.
Then the world changed. The cloud is everywhere, every company has a thousand unsecured remote endpoints, and no one has any idea what "zero trust" means beyond being something their last situationship ran on.
You need a solution that addresses threats already inside your network because perimeter-based security is dead, buried, and maybe zombified. Let's break down what zero trust actually is, why your current setup might need an upgrade, and how to build a strategy that assumes nothing but verifies everything.
Table des matières
What is zero trust security?
Zero trust is a security architecture that flips the script on traditional "castle-and-moat" security. Rather than assume everything inside a corporate network (think devices, users, apps, etc.) is authorized to be there, you treat everything as a threat until proven otherwise, much like how my dog treats Mylar balloons.
It has a simple core philosophy: "never trust, always verify." Every access request inside and outside the network undergoes scrutiny via strict identity verification, least-privilege access, continuous monitoring, and other authentication controls.
Zero trust vs. traditional security
I like to imagine zero trust security models through the lens of airport security, mostly because airport security is the one thing more paranoid than a cybersecurity team:
Traditional (castle-and-moat) model: Once past TSA, you're free to wander around, browse bad souvenirs, or buy a $27 bagel without checkpoints.
Zero trust security: Even after TSA, you get re-screened at each gate, lounge, and before boarding the flight.
This is exactly how zero trust treats your network. Every cloud app, employee login from an outside device, integrated IT system, and remote desktop is a potential entry point for attackers. Employees can connect from anywhere, which also means they're vulnerable from anywhere. Zero trust is your best shot at staying one step ahead of potential threats.
Traditional security | Zero trust security |
|---|---|
Anything inside the network is trustworthy by default | Never trust, always verify (no implicit or assumed trust) |
Hard network boundaries (firewalls) | Fluid boundaries around every resource |
One login = broad network access | Least privilege per session, per resource |
Verify once at entry | Continuous verification for every request |
Focus on external threats | Assumes threats exist inside and out |
Easy lateral movement for attackers | Microsegmentation blocks movement |
Hard network boundaries (firewalls) | Fluid boundaries around every resource |
Tip: If someone asked you right now to list everything connected to your network, could you? If not, you're already operating in zero trust territory whether you know it or not.
How zero trust works: Key components and implementation
Let's clear up a common misconception: zero trust isn't a tool you can buy off the shelf. It combines security practices and controls into one layered system with the goal of establishing a zero trust network architecture.
Here's how the pieces fit together.
Zero trust network access (ZTNA)
ZTNA is the muscle behind the model. It forces users to undergo constant authentication and device verification before they access anything—apps, databases, files, etc.
Compare that to traditional setups that use virtual private networks (VPNs) to connect users remotely. Once a user logs in through the VPN, they can access everything. That's like handing out a master key to every IT resource.
Zero trust access creates encrypted, one-to-one tunnels between a user and only the resource they need. Nothing else. It leans on identity and access management (IAM), network access control (NAC), and endpoint security tools to enforce:
App-level access: CRM access for a salesperson? Yes. The HR database? Nope.
Context-aware checks: Trying to log in at 3 a.m. from an unpatched laptop with a foreign IP? Access denied.
This is where the "layered" security approach plays a role. Even if attackers stole credentials, ZTNA's multiple authentication protocols and least-privilege policies limit the damage.
Integrating with industry standards (NIST 800-207)
The NIST 800-207 is the gold standard for zero trust architecture. When organizations look to revamp their network security, they can look to this framework outlining how to:
Verify identity with multi-factor authentication
Segment networks and IT assets
Enforce least-privilege access policies
Monitor for intrusions or anomalies
It's basically a rulebook that keeps zero trust from turning into a free-for-all. And many compliance requirements use it as their framework.
If you work with federal agencies, for instance, NIST compliance isn't optional—it's required. Programs like Cybersecurity Maturity Model Certification (CMMC) and Federal Risk and Authorization Management Program (FedRAMP) demand adherence to this standard.
Stages of implementation
Zero trust isn't something you slap on your network like a security tag. It's a status you build toward—like inner peace, or a functioning printer. Implementation is an ongoing three-step cycle.
1. Visualize
Welcome to the planning phase, where you channel your inner war general (or your inner Jordin Sparks) because yes, it's a battlefield out there. And before you can defend anything, you need to figure out what's potentially under attack.
Inventory every user, device, app, data flow, and IT resource living on your network, and figure out how each connects to one another.
Find the mission-critical stuff like customer data, financial systems, or anything that would cause mass panic if it vanished.
Hunt down any rickety backdoors—those outdated tools, forgotten email servers, or unpatched systems that might as well have a neon "hack me" sign on them.
2. Mitigate
Now that you know what's at stake, it's time to lock things down.
Break your network into smaller zones with microsegmentation, so if one area gets hit, the rest doesn't go down.
Deploy MFA for your devices and apps.
Apply monitoring tools to surveil the network.
3. Optimize
Once you have a decent perimeter, widen the net.
Extend your watchful gaze to shadow IT (apps or services employees use without permission) and internet of things (IoT) devices.
Fine-tune your zero trust policy so security doesn't hinder productivity (e.g., fewer annoying MFA prompts for low-risk actions or applying SSO).
Tip: Prioritize where you're most vulnerable by starting with your most breached department. (Looking at you, Finance!)
Leveraging analytics and threat intelligence
Every potential breach and network event is a learning opportunity. And zero trust uses analytics to constantly improve itself by using:
Behavioral analytics: Build profiles of what "normal" looks like for users and devices. If Colin from Accounting always logs in from D.C. at 9 a.m., but suddenly shows up at 3 a.m. from Moscow? Flag it.
Enterprise telemetry: Pull in data on device health, app behavior, and network traffic to continuously enforce policy. If your laptop starts acting weird, zero trust notices.
Threat intelligence feeds: Learn from attacks happening elsewhere. These feeds bring in known indicators of compromise (IoCs), emerging tactics, techniques, procedures (TTPs), and leaked credentials so you can proactively adjust defenses.
Why is zero trust essential for modern security?
Your network isn't what it used to be. It's scattered across cloud services, remote workers' home offices, and that coffee shop with the sketchy hotspot (and kombucha).
We're also way more connected to third parties. How many outside organizations have some level of access to your systems? Your accountant, marketing agency, HR consultant, suppliers—each connection is a potential security risk.
Meanwhile, cyber threats have become sophisticated enough to make your old security measures look quaint. New ransomware strands, attack vectors, TTPs—all this leads to why a zero trust security framework is so vital for modern security:
Built to stop current et emerging threats: Newer attack methods (like supply chain attacks and updated ransomware) are always monitored so zero trust can act accordingly.
Actually secures remote work: We don't have to pretend personal devices and random Wi-Fi spots are "trusted." Every login at every location is scrutinized for security.
Tangible cost-cutting benefits: Companies with mature zero trust implementation often save millions during a data breach compared to those who didn't get the memo.
Checks the compliance box: Most security regulations and guidelines include zero trust principles. No more stressing about your next audit.
Builds resilience: Even if you're initially breached, threat actors are stopped in place and can't move throughout the network.
Core principles of zero trust
What I like most about zero trust is it's the security strategy equivalent of sleeping with one eye open, clutching a fire extinguisher, and trusting no one, even if you've worked here for ten years and once brought donuts to a team meeting.
1. Continuous monitoring and validation
Say goodbye to the one-and-done login. Zero trust authentication separates from the VPN connection by:
Checking if your device is still secure (patched, encrypted, MFA-enabled)
Verifying whether user behavior is suddenly sketchy (why is HR downloading the entire payroll database, or a login happening from Serbia?)
Revalidating permissions mid-session (this person isn't supposed to have access to our accounting spreadsheets)
2. Least privilege access
No more "everyone gets admin" because someone didn't want to make a help desk ticket. Your salespeople should only touch sales stuff, Accounting should only touch numbers, and Marketing should stay far away from the firewall configs.
Zero trust keeps everyone in their lane by giving them only what they need to do their job. That way, when someone inevitably clicks a suspicious link, the blast radius is contained.
3. Microsegmentation
A zero trust strategy means dividing the network into smaller sub-networks via access controls and various authentication protocols.
A high-security prison doesn't keep everyone in the same cell block. So why keep all your data, apps, and IT resources in one network?
If hackers breach one, they hit a dead end because the rest stay locked down.
4. Preventing lateral movement
Attackers love "island hopping." They'll compromise an endpoint, then use that endpoint to enter tools or databases, and then use those to adjust the admin settings for higher privileges. Zero trust security solutions cut these excursions short.
New connection? Re-authenticate.
Trying to move from accounting to sales segments? Denied.
Even internal traffic gets re-inspected after time has passed or there's a contextual change.
5. Multi-factor authentication
For a cloud app, all you need is a username and password, and you're in. So when credentials get compromised, attackers have a clear runway to cause havoc.
But what if there was another roadblock? MFA adds an extra layer—like a push notification, fingerprint, or security key—to make sure you are, in fact, you. Because if someone's gonna get in, they better work for it.
6. Device access control
In zero trust, every endpoint device has its own set of auto-enforced rules:
Only company-approved phones, tablets, and computers get into the network.
Endpoints must meet strict security standards (patches, encryption, MFA, etc).
They're always monitored for compromising signals (scanned for malware, anomalous activity, etc).
7. Breach assumption (integrating proactive measures)
The real heart of zero trust is its fatalistic realism. Zero trust doesn't ask if you'll get breached. It assumes you already have.
So act accordingly: monitor everything, keep your data encrypted, re-authenticate constantly, and prevent lateral movement after a breach.
Cyber resilience isn't preventing an attack; it's your ability to minimize its impact.
Key pillars of a zero trust architecture (CISA model)
The Cybersecurity and Infrastructure Security Agency (CISA) breaks down the five make-or-break pillars to help organizations achieve zero trust maturity. Focus on these, and you're golden.
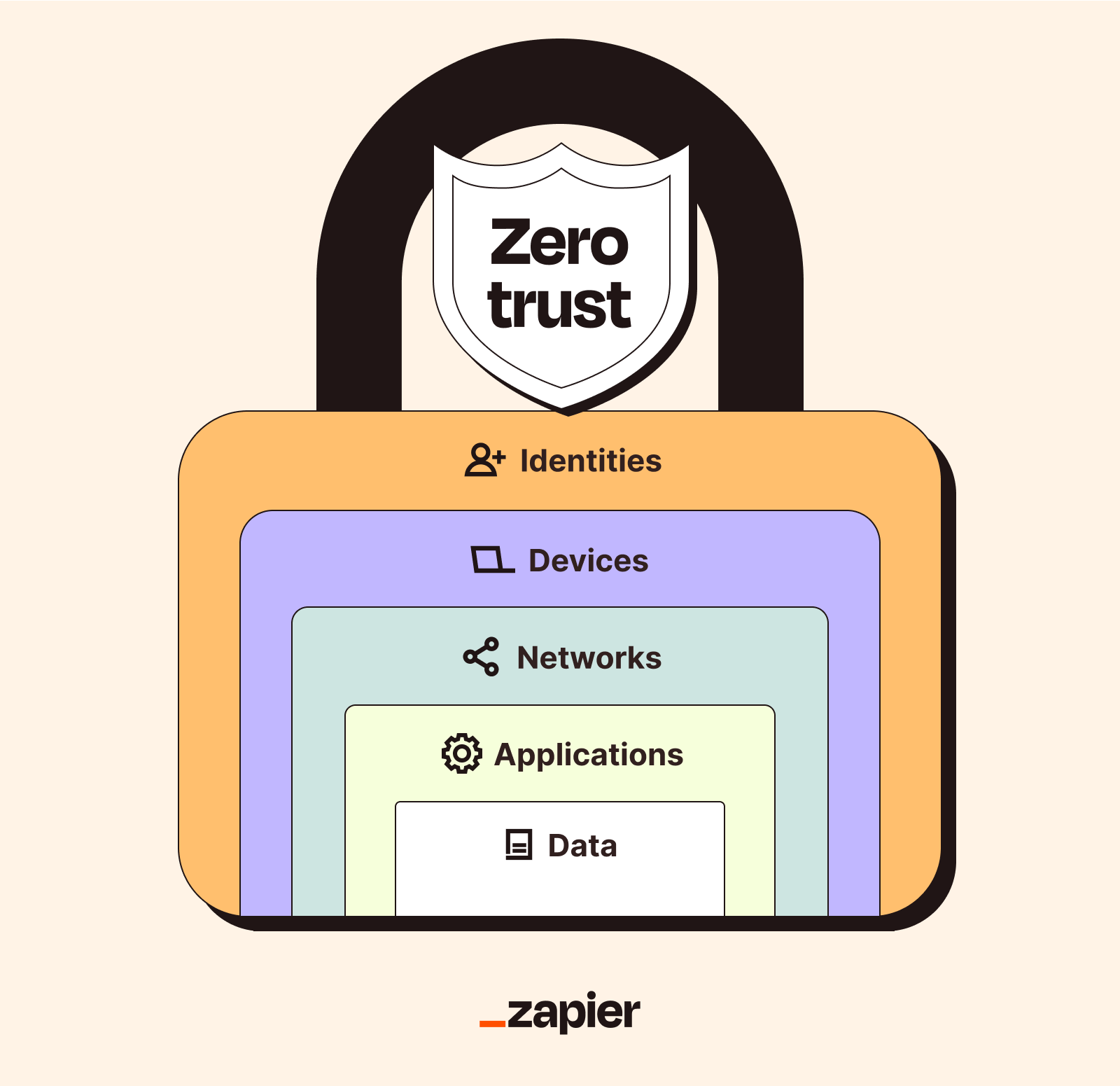
1. Identity
Is that really you logging in? Prove it. Adopt these security tools to ensure authorized access:
Identity access management: Automatically enforce who can access what IT resource based on role, privileges, device, etc.
Single sign-on (SSO): Provide one secure login so users can access everything simultaneously. (Those sticky notes with 20 different passwords are getting pretty annoying.)
MFA: Passwords aren't enough. Throw in a biometric (thumbprint) or a separate PIN to add another layer of security.
2. Devices
Every phone, desktop, tablet, and IoT device is an entry point for attackers. Are you tracking them?
Inventory everything: If it connects to your network, it gets registered. No exceptions.
Compliance checks: Is it patched? Encrypted? Running legit software? If not, update it or take it off the network.
Block the unauthorized: No, your CFO should not be using their personal laptop to check emails or review the books. Either disconnect it or log it (then enforce zero trust policies).
3. Networks
Contain cyber breaches through microsegmentation. Rather than one all-access login, you can operate using smaller networks via software-defined networking (SDN). Tools like Cisco ACI and VMware let you view and control apps and how they connect to one another. SDN essentially lets you create "walls" between different systems.
You should also encrypt everything inside the network (BitLocker, FileVault, and VeraCrypt are popular encryption tools) and replace VPNs with ZTNAs.
Your network should be like a watertight submarine with numerous compartments. One leak shouldn't sink the whole thing.
4. Applications and workloads
Apps are helpful little productivity gremlins until one of them becomes a backdoor for hackers. Yes, Slack can expose your Google Drive if you're not careful. (No one tells you that part during onboarding.) It's why gatekeeping and vetting your APIs is a must.
App access should be constantly checked and reauthorized, and you should continually monitor for unusual behaviors. If your software starts acting possessed (deleting files, eating memory, random permission requests), it might be hacked—or sentient. Either way, shut it down.
5. Data
Ultimately, data is what hackers want. So protect it at all costs. Encrypt your files and records while in transit, in use, or at rest.
Zero trust also means categorizing data based on the use case and importance to the operation. Not all data is created equal. Customer credit card info is far more sensitive than sales deal records. Which is most prone to a breach? Who needs to access it?
All this lets you assign role-based access controls and prioritize security efforts.
Common zero trust use cases
When it's time to retire the traditional security model, here's where zero trust offers the ideal replacement.
1. Replacing or augmenting VPNs
VPNs have a tunnel vision problem. One successful login gives a hacker (or a negligent user) broad access to the entire network. And don't even get me started with the performance issues and lag time plagued by VPNs.
ZTNA is more granular. Need HubSpot access or a suite of apps? That's what you'll get—nothing else. And since the connection is direct to the app, you just need steady Wi-Fi to keep things running smoothly.
2. Securing remote work and third-party access
Traditional security doesn't support remote connectivity or third-party access. That HR director living in Chicago needs to view employee records—even though their company is HQ'd in Seattle. And that "trusted" vendor account is now a backdoor option for a cyber threat.
These unmanaged endpoints and remote users killed the traditional perimeter and left you vulnerable. Zero trust uses continuous verification, least privilege, and device posture checks to plug the holes.
3. Comprehensive cloud and multi-cloud security
Cloud environments break the old security model. AWS security doesn't coordinate with Azure (providers are siloed), and employees can easily spin up their own servers or apps on demand (the shadow IT problem).
How do you maintain consistency in security policies, encryption, and access logging? With zero trust.
One policy to rule them all: Enforces access rules across all cloud providers (AWS, Azure, Google Cloud, Alibaba Cloud)
Workload authentication: Verifies every API call and login, not just the first one
Auto-blocks unknown services: Unapproved cloud instance? Shut it down
4. Onboarding new employees and contractors
Remember way back when manual IT provisioning was a thing? New hires had to wait days before hitting the ground running with tools and a VPN, and interns somehow had admin privileges.
Meanwhile, zero trust lets you onboard precisely in minutes using security automation:
Instant, role-based access: Engineer? Here's GitHub. Marketer? Here's Canva.
No VPN queues: Apps are accessible anywhere, securely.
Auto-offboarding: When a contractor's gig ends, so does their access.
5. Enhancing IoT visibility and security
Think of all the intelligent devices at the office: printers, smart thermostats, voice assistants, sensors, Ring cameras. These dark horse entry points are attached to your network, often run on outdated software, and likely still use the original "admin" passwords. They're begging to be targeted.
Zero trust creates an IoT lockdown. Every device is profiled, segmented from sensitive parts of the network, and uses encrypted comms to prevent outside data sniffing.
Tip: Is your business using AI? Cool. Also terrifying. Check out the top risks AI poses to your company and how to keep them at bay.
How to implement zero trust security (and best practices)
A half-baked zero trust implementation will leave gaping holes in your security posture. Here's how you can nail it:
Prioritize visibility and monitoring: You can't know enough about who or what is on your network. Bring in tools (SIEM, behavior analytics, and NTA systems) where you can see and analyze everything happening.
Maintain device hygiene: Legacy devices have to go. Replace older apps with newer, more secure ones, and don't forget to constantly patch/update your security systems and reinforce endpoint controls.
Strategic network partitioning: Don't let hackers roam freely. A zero trust platform thrives on microsegmentation. Apply SDN and demand that every move through the network has a re-authentication requirement.
Embrace security keys for MFA: Adopt hardware-based tokens like YubiKeys or biometrics for the strongest authentication methods.
Balance security with user experience: Being "too" secure can actually make you less safe. Why? Because burdensome measures lead to circumvention. Find solutions easy for users to get on board with. Context-aware policies, self-service account recovery, and SSO, for instance, are simple ways to make users happier.
Automate your security applications with Zapier
Strong security is more than having the right tools. Zero trust enforces safe security behaviors and designs your IT network to withstand modern cyberattacks.
And with Zapier, you can securely orchestrate your IAM, SSO, MFA, and other security apps in one place, making it easier to incorporate zero trust principles without adding extra manual work.
Lectures connexes :