When you work on a small team, you're extremely busy and focused more on increasing your revenue than protecting your infrastructure. Unfortunately, attackers are aware of this and find small businesses to be an easy target.
When launching my business, I certainly didn't pay much attention to security. It wasn't because I didn't care about it—I just wasn't aware of how common and devastating cyberattacks could be. But now that I'm part of the small business community, I see it happening everywhere. It's not uncommon for me to see comments on Facebook groups from people who've recently started a blog for their business saying they got hacked.
Cyberattacks cost your business time and money, and if sensitive information about your customers gets out, it could also ruin your reputation.
One of the simplest ways to avoid cyberattacks is to make sure each individual at the business is taking steps to help—especially if the majority of employees are working remotely.
The tips here are mostly to protect your computer and software. If your business runs on WordPress, here are some free WordPress security plugins to help protect your website.
Common types of cyberattacks
Before I show you what I do to secure my infrastructure, I want to quickly go over some of the most common attacks small businesses face.
Phishing. These are emails pretending to be from your bank, internet service provider, or other places that aren't who they say they are. They typically want you to click a link so they can gather some type of personal information from you.
RAT. A Remote Access Trojan allows attackers to access your computer's camera and microphone, and install other types of malware.
Keylogger. This one records everything you type on your keyboard (terrifying enough for you?), and it's often used to steal passwords and credit card details.
Shoulder surfing. This is when attackers gather personal or private information by simply looking at your screen.
Malware attack. Malware is any kind of malicious software meant to harm or exploit a device, service, or network. It's an umbrella term, and it includes things like viruses, Trojans, worms, ransomware, and more.
Man-in-the-Middle attack. A MitM attack intercepts the communication between you and the server. For example, if you wanted to log in to your bank account, the attacker would receive your login information and then send it to the bank, the bank would then send the response to the attacker, and the attacker would send it back to you. This is very common when connecting to public Wi-Fi.
What each team member can do to secure small business infrastructure
Each business will need different security measures, but there are a few things employees can do on their own to help. Send this list to the rest of your team, add it to your standard operating procedures, and make sure that everyone on the team is following these best practices.
1. Don't leave your computer unattended
One of the coffee shops I frequent the most to do my work doesn't have a restroom inside. So in order to answer nature's call, I have to leave the coffee shop, walk over to the building next to it, and go up to the third floor.
This means that anyone wanting to take a peek at my computer, install malware, or simply steal it, would have plenty of time to do it. To prevent any of these things from happening, I just put my laptop inside a sleeve and take it with me.
Since it's a small coffee shop, it's pretty easy to lose my spot, so I typically leave my backpack on top of my chair and my headphones on the table. Obviously, I don't keep anything of value inside the backpack (it's often empty) in case someone decides to take it.
I know that not leaving your belongings unattended might sound obvious, but I see it happening almost every time I go to the coffee shop. Even if it's just for a minute or two, that's enough time for someone to download malware or steal your laptop. Just take your stuff with you—it's not worth the risk.
2. Use a VPN when connecting to public Wi-Fi
A few years ago, I used to travel a lot for work, which meant I had to connect to many unsecured Wi-Fi networks in airports and hotels. The issue with these types of networks is that hackers can position themselves between you and the connection point—Man-in-the-Middle attacks.
So instead of your data going directly to the hotspot, it goes to the hacker, who then sends it to the hotspot. This gives them access to anything you send over the internet, which could be emails, bank statements, credit card information, your website's login information, the list goes on. Basically, they can access your systems as if they were you.
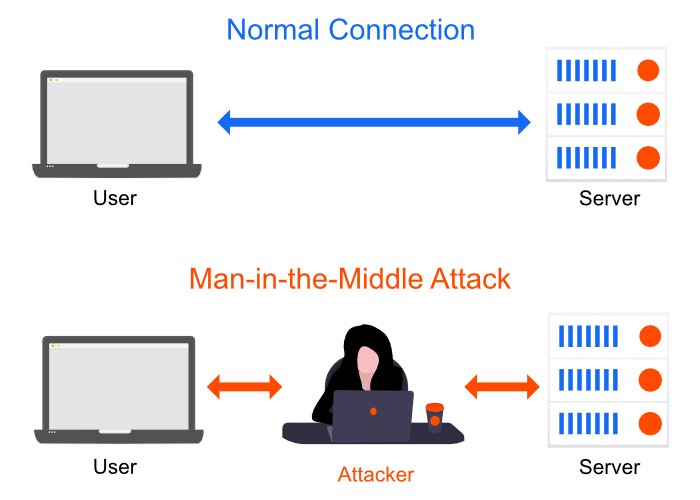
Other common things hackers do with these types of unsecured connections are distributing malware and creating fake connecting points to connect to.
To protect myself from these attacks when connecting to public Wi-Fi, I use a virtual private network (VPN) called CyberGhost. One of the things a VPN does is encrypt your data traffic, so that even if an attacker gets their hands on it, they won't be able to decipher it because it'll show as a bunch of gibberish to them. Since hackers typically go for easy targets, once they see that you have a VPN set up, they'll simply skip you and go on to the next victim who isn't protecting their data.
3. Use a privacy screen
One thing I saw a lot when traveling was people opening up their laptops in the airplane rows in front of me and working on what was obviously sensitive information. If I'd been interested in learning more about their jobs or stealing their information, I could have easily done it.
If I could see other people's screens, that meant they could see mine. So to prevent people from shoulder surfing me, I use a privacy screen. It's essentially a piece of plastic you put on your laptop screen that allows only someone directly in front of the computer to see what's going on. Anyone looking from the sides will see a completely black screen.
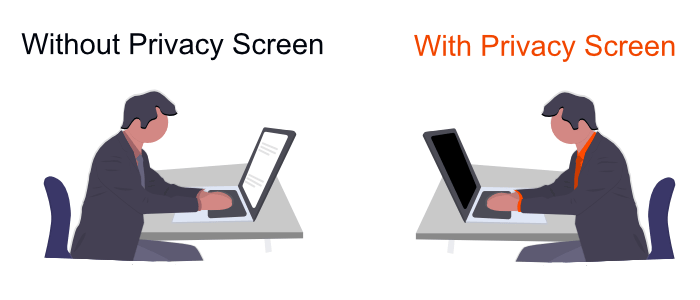
There are plenty of privacy screen brands you can get online, but the brands I've liked the most are SightPro and Akamai. I've tried super cheap ones as well, but they always ended up deteriorating fairly quickly. I guess it's true what they say: "Buy nice or buy twice."
4. Don't click on unknown links
I'm also very wary of clicking on links in emails. A lot of people think that as long as they don't download anything, they'll be safe. But even clicking a bad link can cause your computer to get infected. And while sometimes they're easy to spot, spammers are getting pretty good at disguising their links to make you think they're legitimate.
Here's an example of an email I received pretending to be from Norton AntiVirus, but it was actually redirecting me to a different website:
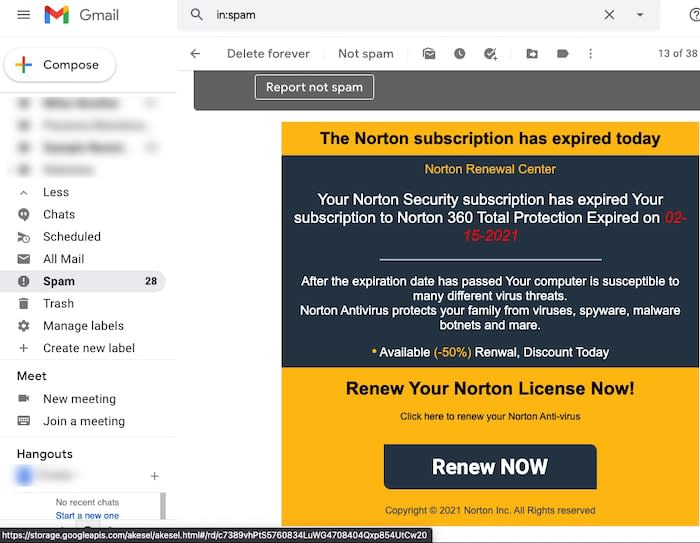
Sure, it's not the best ripoff of Norton branding, but if I were doing a quick email cleanup, I might not notice. So, before clicking a link, no matter who it's from, I always hover over it to see where it actually goes. The real website is typically shown at the bottom-left corner of the browser screen, as you can see in the image above.
I also get the occasional spam comment with weird links on my website. Clicking any one of those unknown links could deploy various types of malware, such as RAT, keylogger, and botnets. If you're bombarded with spam comments, you can block them using a plugin like Akismet. Another option (and the one I use) is to copy this list of common strings used by spammers to automatically send those comments to the trash.
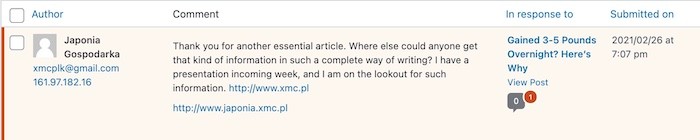
Simply copy all the strings on that list, and then go to your WordPress dashboard > Settings > Discussion > Disallowed Comments Keys > paste the strings > Save Changes.
5. Keep everything up-to-date
Apps seem to require updates all the time, which can seem annoying. But those updates contain important fixes to known vulnerabilities that hackers can exploit to install malware, steal your data, or do any other type of harm to your system.
You can automate the process of keeping things up-to-date. Here's how to enable automatic updates on the two most popular operating systems:
How to enable automatic updates on macOS
Open the App Store > Click App Store on the top menu > Preferences > tick the Automatic Updates box.
How to enable automatic updates on Windows
Open the Microsoft Store > click the three dots on the upper-right corner > Settings > App updates > turn on Update apps automatically.
While you're at it, it's worth doing the same on your phone.
6. Use full-disk encryption
As a small business owner, I have lots of private information on my computer, including banking information, business plans, account numbers, taxes, client data, and more. Having someone access some of this information, especially my clients' data, could seriously damage my business and reputation—not to mention the harm it would do to the client.
If your business stores things like personal health information (PHI) from your clients, and this information gets revealed, you could face huge fines and even jail time for allowing the breach. The HIPAA and FINRA regulations are justifiably strict.
Without full-disk encryption, if someone steals your laptop, they can access the data on your drive, even if you have a password protecting your login: they can simply remove the drive and install it on another computer. With full-disk encryption, they won't be able to see anything that's inside the drive since it'll all be encrypted.
Both macOS and Windows come with free full-disk encryption, which should be enabled by default. However, if yours isn't enabled, you can follow these steps.
How to enable full-disk encryption on macOS
If you're using macOS, then FileVault is the program you want to activate. To do this, click the Apple logo on the top-left corner > System Preferences… > Security & Privacy.
Then, click the FileVault tab > Click on the lock icon at the bottom-left of the window > enter your password > Click Turn On FileVault.
How to enable full-disk encryption on Windows
If you're using Windows, click on the Start button > Settings > Update & Security > Device encryption > click on Turn on.
7. Create regular backups
Creating regular backups is a good way of preventing ransomware, a type of malware that holds your data hostage by encrypting it and demands a payment to release the data back to you. If you make regular backups of your data, you can simply wipe your computer, reset it to factory settings, and restore your data from the backup.
I like keeping my backups in an external hard drive instead of the cloud. While it's not as convenient as simply connecting to the cloud and uploading your files, it keeps everything in a secure off-site location.
I typically create backups every month, but if you're constantly creating important information, you can do them weekly or daily. My favorite brand for external hard drives is Western Digital (WD), but Samsung also makes good options.
How to create backups on macOS
To create backups, I like using macOS' built-in backup tool called Time Machine. The cool thing about it is that, once I plug in my hard drive, it works automatically in the background. It continuously saves copies of all my files, apps, and any other important information and excludes useless files in the trash, cache files, and logs.
To use Time Machine, plug in your external drive > go to System Preferences > Time Machine > toggle the switch to On > Select Disk… > select the drive you want to use.
In order to use the drive, it needs to be formatted as macOS Extended (journaled). If yours isn't, Time Machine will ask if you want to reformat it, which will erase all the existing files on it.
How to create backups on Windows
Windows' built-in backup tool is called File History. To start backing up data on Windows, connect your external drive > click Start > Settings > Update & Security > Backup > Add a drive > select the external drive where you want to store the backups.
8. Use strong passwords
Growing up, I used to use the same password for everything. To be honest, I still use it, but only for accounts that don't really matter—like the email account I use to sign up for random newsletters to get coupons and discounts from stores.
When it comes to things like my website, laptop, bank accounts, email, and other products that require me to add more personal information, I go ahead and create longer and more difficult passwords that include mixed characters like numbers and symbols.
But now I've reached a point where I have too many accounts, so keeping track of all of the passwords is a nightmare. To create and store complex passwords, I use the free version of a password management tool called LastPass (you can compare it to the other popular option, 1Password, using Zapier's password manager showdown). It has an autofill option that automatically fills usernames and passwords when visiting websites, so you don't have to copy/paste them.
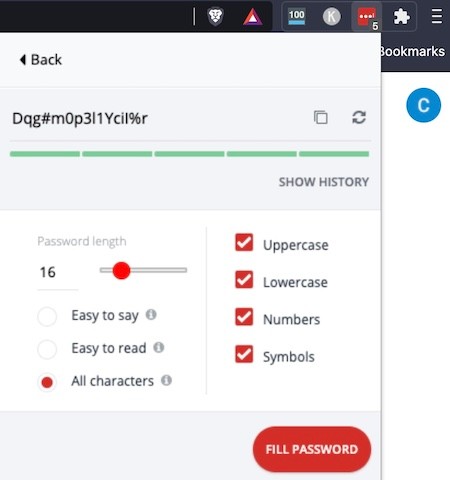
Besides keeping everything secure on LastPass, I also like keeping a hard copy of my passwords in a safe place at home, just in case something happens to LastPass or I don't have access to it. If you do write your passwords on a sheet of paper, make sure that you place them in a secure place—i.e., not behind your computer monitor or under the desk.
If you don't want to install the LastPass extension but want to create strong passwords, you can just use the free password generator tool on their website.
9. Use two-factor authentication (2FA)
Two-factor authentication (2FA) means you need to verify your identity in two unique ways before you can access a website or app.
For example, if you enable 2FA for your email account, once you enter your username and password, you'll be asked to enter a unique one-time access code sent to your phone via text or an authenticator app like Microsoft Authenticator, which is the one I use.
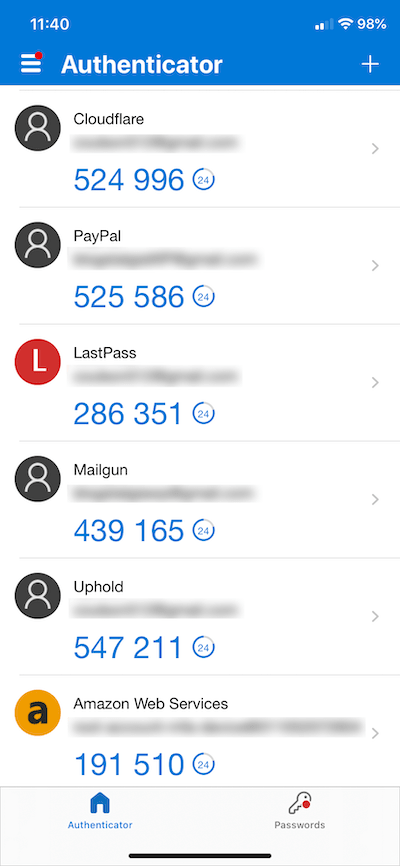
So, even if someone knows your email and password, they won't be able to access the system without your phone.
If I'm completely honest, I dislike using two-factor authentication. My issue with it is that I have so many accounts it becomes a little annoying having to go to my phone and verify my identity every time I want to log in.
Still, I'd rather be safe than sorry, so I enable it for important accounts, such as my bank accounts, emails, and websites. If you have online accounts with important information that support two-factor authentication, I recommend enabling it.
If everyone on your team follows these relatively simple steps, it'll add a massive layer of protection against cybercriminals. After all, cyberattackers (usually) want easy targets, so simply by not being one, you're decreasing your risk.