"Plain email is not a secure medium." - The SANS Institute
According to the Breach Level Index, over 13 million records have leaked or been lost in published cybersecurity breaches since 2013. Of those 13 million records, a terrifying 96 percent weren't encrypted. The method these hackers most often use to break in, steal staff identities, and mine trade secrets?
Email.
Email is ancient technology compared to modern team communication tools, and it has technical limitations that make its age a real barrier to security. Luckily for its four billion users, developers and security researchers are consistently coming up with ways to improve on this old technology for it to be viable and safe in the age of rapid and intelligent attacks.
In this piece, we'll talk about what to look for in a secure email service, and then we'll present what we found to be the seven most secure services.
Security Features to Look for in an Email Service
You probably already use Gmail or Outlook. What's wrong with those services? Are they not secure? Well, it depends on your threat model and adversary.
Some of the biggest differentiators between security-focused and regular email are pertinent if you're a large organization or enemy of the state, but could be seen as overkill by everyday users.
For example, server location might only be pertinent if you're an activist who can reasonably expect their communications to be subpoenaed by the government. On the other hand, end-to-end encryption can help both individuals and businesses keep their information secret: Unencrypted emails were to blame for at least four major breaches of the past few years, leaking millions of emails and causing millions of dollars of avoidable damage.
Below are the features you'll often find as part of secure email, along with thoughts on why they may—or may not—matter to you.
End-to-end encryption
To understand end-to-end encryption, you first need to understand encryption.
Encryption is a way to obscure data. Any website with https in its URL is using Secure Socket Layer (SSL) to keep data you send secure as it travels from your computer to the website's server. SSL provides a way for your computer to guarantee that data it sends to and receives from an SSL-enabled server is encrypted. Almost all websites you visit regularly will have SSL enabled to protect users against getting their passwords or form input stolen by someone "tapping the line."
The same goes for email data: Sending an email over an encrypted network means scrambling the plain text content of the email so it's impossible to read without what's called an encryption key, which functions like a password.
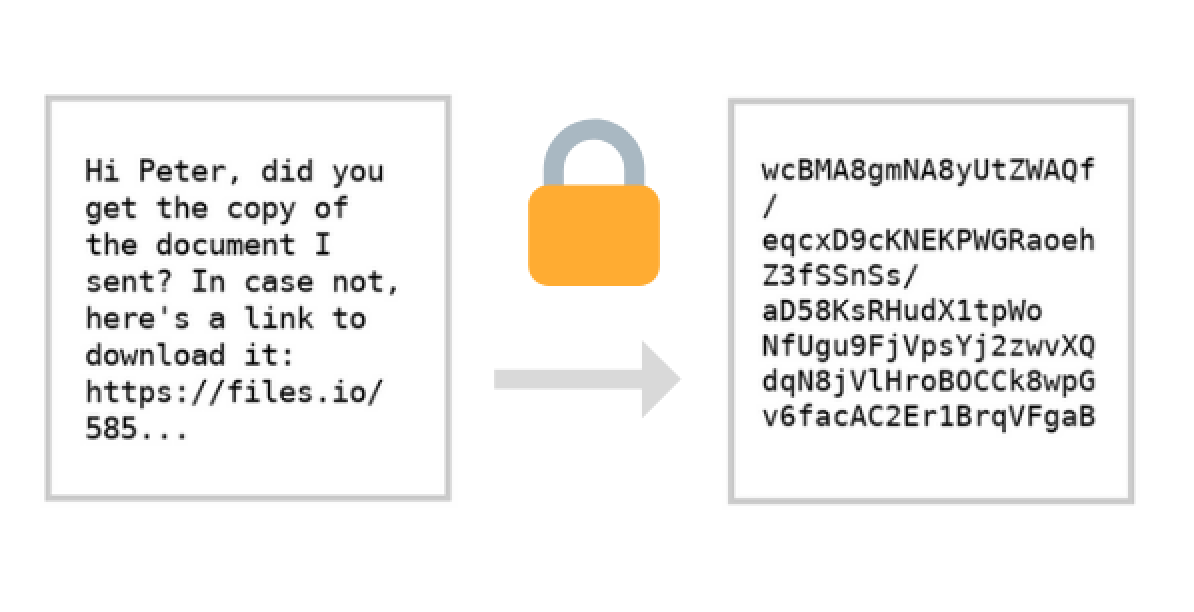
Modern encryption does such a good job that it would take a million computers working for sixteen million years to crack, but non-security focused services like Gmail and Hotmail only encrypt the data as it travels from your computer to their servers. On the other side, it can be plainly read. That requires users to trust that these organizations won't use their encryption keys to read your email—or that the keys won't fall into the hands of hackers.
End-to-end encryption puts control in the hands of the user. When you load up your inbox from an end-to-end encrypted email service, it first has to receive a private key that's unique to your account—and essentially uncrackable—before it de-scrambles the encrypted content. Unless you're manually encrypting emails, this process all happens in the background for end-to-end encrypted tools.
Encryption is a hard problem to solve for computer scientists and can be resource-intensive to implement. It's only in recent years that end-to-end encryption has become standard thanks both to messaging apps like WhatsApp and the public's increased paranoia after incidents like Snowden's NSA leaks, which revealed the extent to which world governments monitor their citizens. Not even Google's systems were safe from prying eyes.
If an email service that uses end-to-end encryption is forced by the authorities to hand over its data, it will only be able to provide data that is useless to anyone without the user's private encryption key.
PGP encryption
Pretty Good Privacy, or PGP, was developed in the early 1990s as a way to guarantee the security and privacy of email communications over insecure networks. Its basic concept involves the use of private and public keypairs, and is implemented today in secure communications tools like ProtonMail and Signal.
When you send an email encrypted with PGP, you use your public key like a padlock to secure the contents, in addition to using your password to authenticate with your email service. The recipient then uses their own private key to unlock the padlock and read the message. Public and private keys are simply long strings of text, like passwords.
Keys can act like an email address, in that people can send emails to your public key. Some tools expose the key functionality to the user (adding complexity), while others just control your keys in the background and handle it all for you.
In the hands of anyone without the private key, a PGP-encrypted message is illegible:
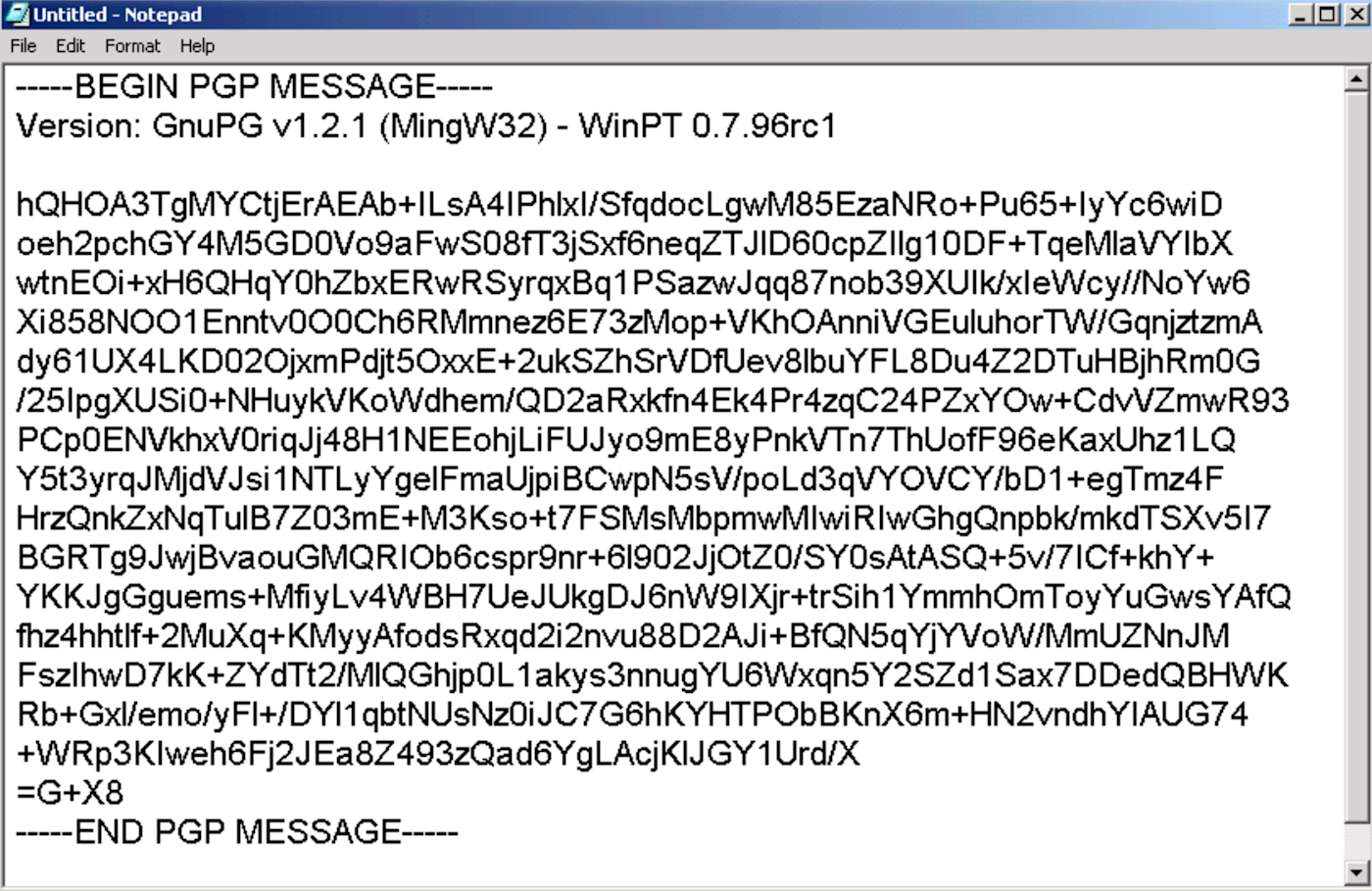
Pasting that block into a decryption tool that is configured with your private key would reveal the contents. That's right: PGP can be done manually without any special email tool. As long as an adversary doesn't crack your hundreds-of-characters-long password, it's one of the most secure methods.
Although it used to be a manual encryption method, many secure email services today build PGP into the back end, so while your emails might arrive in plain text, they're total gibberish behind the scenes. (It's worth noting that none of this matters if an adversary manages to find out your password.)
One differentiating feature for secure email is whether the service allows you to have control over your own encryption keys, i.e., the ability to swap these keys out for ones you have previously used.
Note: PGP is open source technology and has been implemented by various developers and organizations. In 2018, it was found that some of these implementations suffer from a security flaw that could allow a hacker to decrypt HTML emails if the account had been previously compromised. This flaw affected email clients such as Outlook, Apple Mail, and Thunderbird, but none of the services on this list.
Two-factor authentication
Two-factor authentication adds an extra layer of security to your email accounts that makes a cracked password useless and the hacking process exponentially more difficult. That's because it relies on two things:
Something you know, like a username and password
Something you have, like your mobile phone or a backup key
It makes sense not to rely solely on the integrity of your password. Have I Been Pwned, a database of sensitive information captured from hacks all around the world, has over 320 million passwords on file. Passwords are routinely hacked, leaked, and used to compromise victims' accounts. The likelihood of a hacker having access to both your password and your phone or physical backup, however, is vastly lower.
Two-factor authentication is implemented in a lot of different ways, but the most common is the use of a one-time token. When you tap the Google app to sign in from a new computer, you're sending a unique token to the server that can be used only once. The same goes for getting a code over SMS to log into Twitter. This prevents it from leaking or being used for continued access. It also makes it easier to recover your account if you lose access.
Open source
Open source software, like the Android operating system and Firefox browser, is software that makes its source code available for users, developers, and the community to inspect and improve. This is contrary to something like Microsoft Outlook, which comes packaged as an executable file that can't be inspected or audited.
What does the way a tool's source code is treated have to do with security?
Well, when you're using an email service like Outlook, you're putting your trust in the fact that Microsoft's developers are (a) acting in good faith by not adding anti-user features to the software, and (b) competent and have built a secure system.
No such leap of faith is required if the software is open source. Open source projects are developed with complete transparency because that's how they thrive and improve. Bugs are made public knowledge, and large projects are armed with thousands of dedicated debuggers.
This kind of scrutiny is good, and it's uniquely possible with open source. In fact, it's one of the reasons Linux operating system was developed so stably and quickly despite being the project of a bedroom hacker and group of volunteers.
Analyzing the merits of the open source model in his book The Cathedral and the Bazaar, developer Eric Raymond writes:
Consider the way a puddle of water finds a drain, or better yet how ants find food: exploration essentially by diffusion [...] Given a large enough beta-tester and co-developer base, almost every problem will be characterized quickly and the fix obvious to someone. Or, less formally, "Given enough eyeballs, all bugs are shallow."
There's nothing about closed source software that implies insecurity, but an open source email service and app is usually desirable because you will be able to review third-party audits and proof. We reached out to Brett Shavers, digital forensics analyst and owner of incident response training firm DFIR Training, to clarify why it's important that a tool is open source:
Open source implies that since the code is open to inspection that it must be safer since you can see the code. But for all practical purposes, few ever check the code of any open source software and trust it anyway. With closed source, you just have to trust it. Either way, most email users simply trust their service. I tend to go with the open source model.
For closed-source projects, you have to take the developer's word for it, and they could be implementing dodgy cryptography.
Metadata handling
Did you know that when you send an email, you're also broadcasting information about your computer, web browser, network, and recipient?
This data is stored in email header metadata, and secure email services usually strip it out. Remember, when you're dealing with security, you're also dealing with smart humans trying to mine available information about your life, habits, and preferences. If you don't think metadata matters, maybe the Electronic Frontier Foundation can talk you round:
Even a tiny sample of metadata can provide an intimate lens into a person's life. [...] They know you called a gynecologist, spoke for a half hour, and then searched online for the local abortion clinic's number later that day. But nobody knows what you spoke about.
Secure email services should strip header metadata out and collect as little data as possible about its users to protect their privacy.
Server location
Server location was hardly a security consideration for the public before it was revealed that Australia, Britain, Canada, New Zealand, and the United States cooperate to share intelligence data about citizens, gathered from servers located inside their territories.
The poster child for this alarming revelation was Lavabit, the now-defunct email service used by Edward Snowden to communicate with human rights activists from his confines in Moscow. Following the forced closure of Lavabit, the email service's founder displayed this message on the site's homepage:
This experience has taught me one very important lesson: without congressional action or a strong judicial precedent, I would strongly recommend against anyone trusting their private data to a company with physical ties to the United States.
It's not just that the U.S. has particularly anti-user laws in this area, but that some countries have laws that respect and fight for the security of user data. Countries with favorable privacy laws include Switzerland, Germany, Belgium, Norway, and Sweden.
Now let's take a look at seven of the most secure email services and see how they stack up.
ProtonMail (Web, Android, iOS)
A mature end-to-end encrypted email service with excellent mobile apps
ProtonMail's servers are locked down under 1,000 meters of solid rock, in a Swiss bunker that can survive a nuclear attack. And its digital security is about as impressive. It began development by a team of CERN Large Hadron Collider scientists in the wake of the 2013 Snowden leak, and has since become the #1 most-used secure email service with over five million users.
ProtonMail is designed with the principle of zero access and zero knowledge, which means that the email servers and staff that work with them have no way of reading or sharing your emails.
Based in Switzerland, ProtonMail data is protected by the Swiss Federal Data Protection Act (DPA) and the Swiss Federal Data Protection Ordinance (DPO), which offers some of the best privacy protection in the world. In the unlikely case ProtonMail was ordered to hand over user data, it would have to be specifically subpoenaed by the Cantonal Court of Geneva or the Swiss Federal Supreme Court. And, even if user data were seized, it would be impossible to decipher because of ProtonMail's encryption:
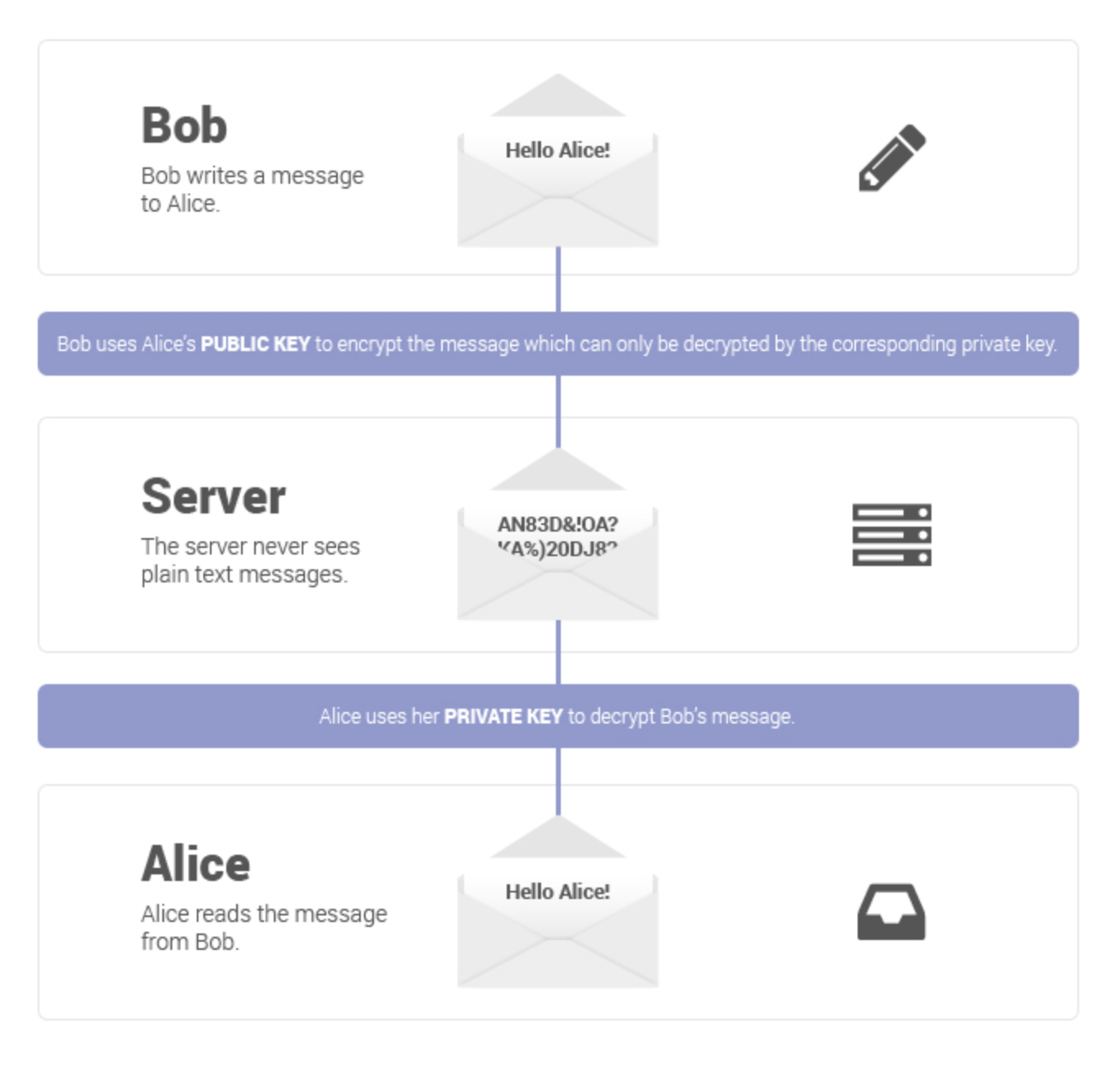
Unlike Gmail or Outlook, email you send with ProtonMail is encrypted before it's sent to the ProtonMail servers. That means that no hacker intercepting emails sent from ProtonMail will be able to decrypt and read your emails.
ProtonMail's encryption and web interface are also open source, which has allowed experts to audit and confirm its high levels of security.
That said, ProtonMail's super-secure encryption can sometimes be a barrier to usability. It isn't possible to add your ProtonMail inbox to a mobile mail app like iOS Mail or K-9 Mail because these generic apps have no way of encrypting emails on the client side, which means ProtonMail won't let you connect in the first place.
Users that don't mind a dedicated app can get ProtonMail for Android and iOS. On desktop, however, you're free to use a variety of popular generic clients as long as you install ProtonMail Bridge, which acts as an encryption layer on top of the client.
ProtonMailPrice: Free plan offers 500MB of storage and up to 150 messages/day; paid plans starting at $4/month (billed annually) for 5GB of storage and up to 1,000 messages/day.
Posteo (Web)
Secure and anonymous email for activists
For just over $1/month, Posteo offers 2GB of secure email storage—completely anonymously and protected by two-factor authentication. Posteo's secure servers are based in Germany, and its values are centered around privacy, usability, and sustainability.
Like a lot of privacy products, Posteo came into the public consciousness after the Edward Snowden leaks. It was the first email service to launch DNS-based Authentication of Named Entities (DANE) on its servers in order to secure users against hackers impersonating them or their email recipients—that is, the man-in-the-middle attacks detailed in leaked NSA documents.
Posteo doesn't just refuse to collect its customers' identities, it also routinely fights legal battles for the right to not turn user data over to the authorities.
Their 2017 transparency report reveals that Posteo received 48 requests for user data and mailbox seizure from German and international authorities, and three requests were successful. However, Posteo does not store identifying data or a user's IP address, so any email content seized isn't able to be formally linked to a user.
Posteo encrypts data you send over its servers while it is in transit and at rest, but doesn't offer automatic end-to-end encryption like ProtonMail and Tutanota. This means that any leaked communications could be read in plain text by an intercepting adversary (although Posteo largely negates this risk with its DANE feature).
Because it doesn't use end-to-end encryption, it's possible to add your Posteo account to stock mail apps on desktop, iOS, and Android.
Posteo Price: €1/month for 2GB of storage.
Tutanota (Web, Android, iOS)
Cheaper than ProtonMail and just as secure
With over two million users, Tutanota is one of the most popular and regularly recommended secure email services. It uses end-to-end encryption, two-factor authentication, and has an A+ SSL certificate. These factors—plus the fact that it's an externally-audited, open source tool—make its security ProtonMail's equal and Posteo's superior.
Like Posteo, Tutanota was one of the world's first services to implement DNS-based Authentication of Named Entities (DANE) in order to secure users against hackers impersonating them or their email recipients.
Since Tutanota uses end-to-end encryption, this means that when you email to someone using a service that isn't end-to-end encrypted, like Gmail, the email arrives password protected as an extra layer of security, and the recipient's replies are managed through a one-time-use version of Tutanota that encrypts their response.
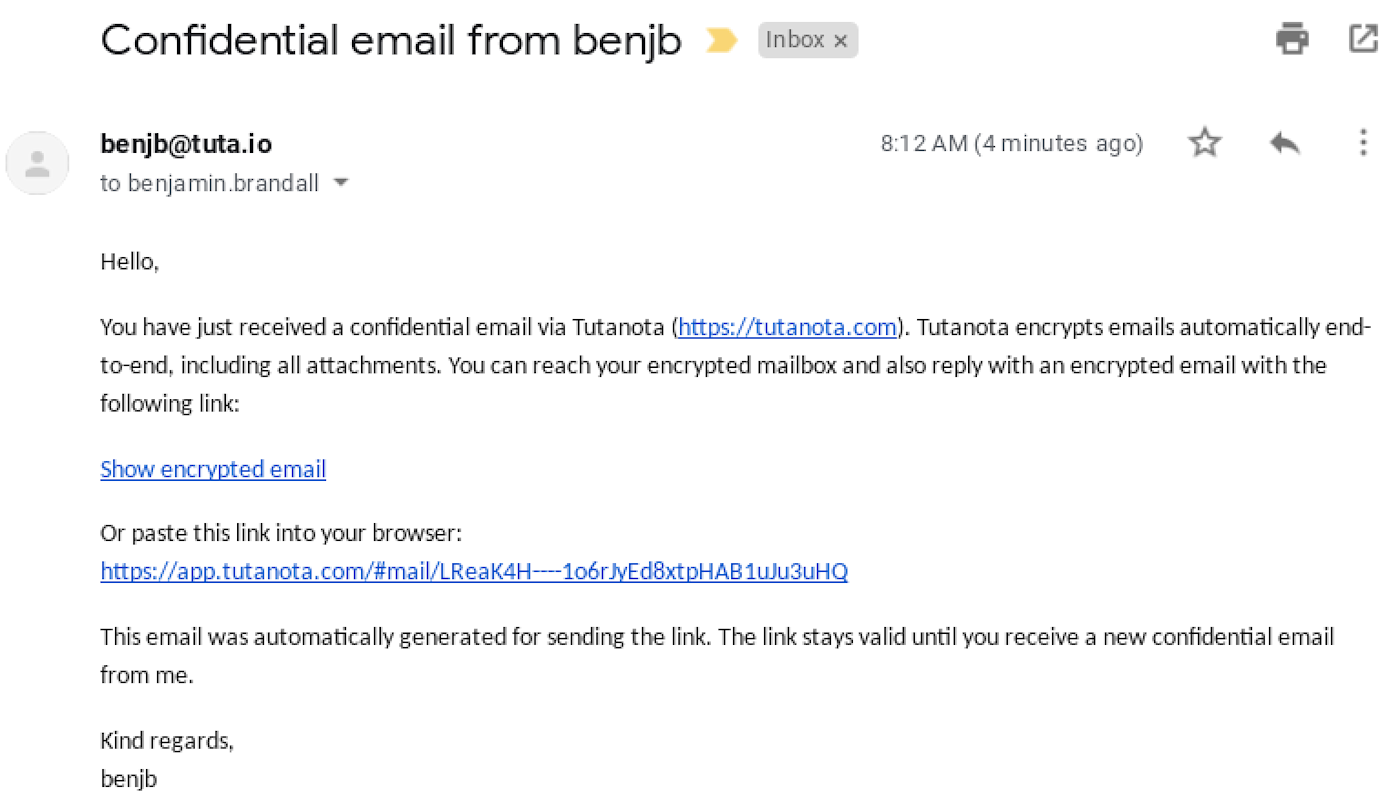
Webmail access is available, alongside native apps for Android and iOS. However, it's incompatible with generic apps like iOS Mail or Android K-9 because end-to-end encryption isn't possible without a client that supports it.
Tutanota Price: Free for up to 1GB of storage; €1/month (billed annually) to unlock premium features like custom domains and filters.
Kolab Now (Web)
An alternative to G Suite and Office 365
With email, calendar, contacts, and file storage, Kolab Now markets itself as a secure alternative to G Suite and Office 365.
Kolab Now was developed for the German Federal Office of Internet Security and mainly used in Germany until it gained mainstream media attention in the wake of the NSA leaks. Groklaw founder Pamela Jones revealed she was moving to a Kolab Now email address on the same day she shuttered the site in 2013:
If you have to stay on the Internet, my research indicates that the short term safety from surveillance, to the degree that is even possible, is to use a service like Kolab for email, which is located in Switzerland, and hence is under different laws than the US, laws which attempt to afford more privacy to citizens.
Kolab Now is completely open source and offers advanced security features. While it's missing end-to-end encryption (outside of its desktop client), it does support perfect forward secrecy (PFS), which means encryption keys are ephemeral: If encrypted content happens to fall into the wrong hands, it won't be usable with any key apart from the disposable one used in that session.
For mobile access, you can use webmail through your device's browser or hook Kolab Now into your POP3/IMAP client like iOS Mail. Kolab Now also supports SMTP, CalDav, and WebDAV protocols, so if your business's systems are already integrated with one of these protocols, that might be a plus.
Kolab Now Price: From $4.41/month (based on estimated conversion from CHF) for individual accounts.
Mailfence (Web)
Another alternative to G Suite and Office 365
Mailfence was launched in 2013 by ContactOffice, a company which has developed cloud collaboration software since the late 1990s. Its servers are located in Belgium, one of the world's privacy havens.
As well as secure email—encrypted with a secure, open source implementation of OpenPGP—Mailfence offers calendar, contact, and document tools in the cloud. This makes it a stronger alternative to G Suite than most others on this list, and a cheaper competitor to Kolab Now with even better security (end-to-end encryption).
Mailfence's end-to-end encryption is interoperable with any OpenPGP-compatible service like ProtonMail or Tutanota. That means that emails sent outside the Mailfence network are still fully encrypted, without the need for the recipient to decrypt it manually. Existing PGP users can also import and manage their own keypairs in the app.
Despite its robust security, Mailfence isn't as user-friendly as Tutanota or ProtonMail. End-to-end encryption is only possible after generating a keypair and uploading the recipient's public key: This level of complexity makes it a poor choice for anyone looking to get encrypted email for the less tech-savvy in their lives.
Mailfence doesn't offer its own mobile apps yet but informed us that clients for Android and iOS are currently in development.
Mailfence Price: Free for 500MB of email storage and 500MB of document storage; from €2.50/month for 5GB of email storage and 12GB of document storage.
mailbox.org (Web)
Time-tested secure email operated by a privacy-conscious journalist
mailbox.org is operated by Peer Heinlein, a journalist and internet pioneer with a long history of providing secure network services, going back as far as 1989. No need to worry that you're putting your inbox in the hands of a shaky startup—mailbox.org has stood the test of time.
Its servers are located in Germany and subject to favorable privacy laws, but it doesn't stop there when it comes to protecting its users. mailbox.org is dedicated to anonymity: It's possible to sign up for an account with no personal information, using Bitcoin, on the service's own Tor relay. Mail headers are also anonymized to hide the location and devices of users and their recipients.
Like Mailfence and ProtonMail, mailbox.org is compatible with OpenPGP, allowing users to send encrypted mail even to non-mailbox.org recipients. Emails sent to users that don't use mailbox.org or an OpenPGP-compatible service will automatically be suspended in a guest inbox where the user can access the message and respond through a disposable link. This is the exact same approach taken by Tutanota for solving the problem of communicating outside your encrypted network (with users on Gmail or other plain-text services).
mailbox.org Price: From €1/month for 2GB of email storage and 100MB of cloud storage.
As you make your decision about which secure email service to use, it's worth also considering which tools security experts trust with their communications.
ProtonMail is the email service of choice for both TV's Mr. Robot and digital forensics expert Brett Shavers:
My personal favorite in webmail is ProtonMail. Easy to use, the basic version is free, and the developers seem to have a solid business purpose. However, Protonmail still requires trust on the user's part. Better is to have control of the encryption keys and configure your email client to use something like Pretty Good Privacy (PGP).
Security consultant and "old-fashioned" PGP user Hamid Kashfi has a similarly skeptical viewpoint:
It's a user's responsibility to have their comms secure and encrypted, not the provider. This way you will never have to worry about your provider selling you out.
For Bruce Schneier, maybe there's a limit to how many layers of security can be frankensteined on top of an insecure protocol from the mid-'90s.
When I need to communicate securely, I ignore email entirely and use Signal.
That says it all.
This article was updated in August 2020 to remove SCRYPTmail as its service has been discontinued.
ProtonMail's encryption image from ProtonMail. Posteo interface image from Posteo.